OWASP IoT Security Testing Guide
The OWASP IoT Security Testing Guide provides a comprehensive methodology for penetration tests in the IoT field offering flexibility to adapt innovations and developments on the IoT market while still ensuring comparability of test results. The guide provides an understanding of communication between manufacturers and operators of IoT devices as well as penetration testing teams that’s facilitated by establishing a common terminology.
Security assurance and test coverage can be demonstrated with the overview of IoT components and test case categories applicable to each below. The methodology, underlying models, and catalog of test cases present tools that can be used separately and in conjunction with each other.
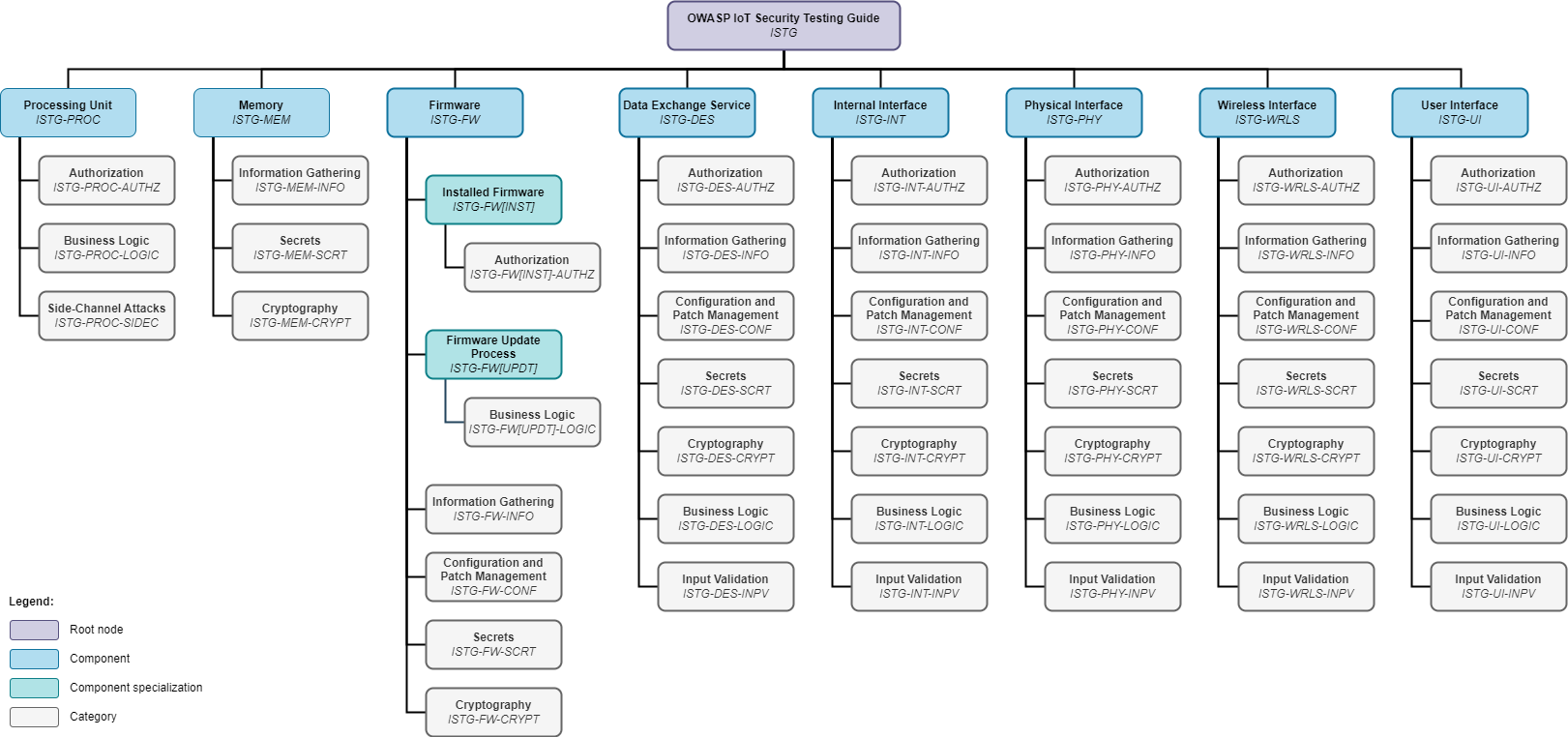
Table of Contents
-
IoT Security Testing Framework
2.1. IoT Device Model
2.2. Attacker Model
2.3. Testing Methodology
-
3.1. Processing Units (ISTG-PROC)
3.2. Memory (ISTG-MEM)
3.3. Firmware (ISTG-FW)
3.3.1. Installed Firmware (ISTG-FW[INST])
3.3.1. Firmware Update Mechnanism (ISTG-FW[UPDT])
3.4. Data Exchange Services (ISTG-DES)
3.5. Internal Interfaces (ISTG-INT)
3.6. Physical Interfaces (ISTG-PHY)
Related Work
The concepts, models and test steps presented in the OWASP IoT Security Testing Guide are based on the master's thesis "Development of a Methodology for Penetration Tests of Devices in the Field of the Internet of Things" by Luca Pascal Rotsch.
Test cases were derived from the following public sources:
- OWASP "Web Security Testing Guide"
- OWASP "Firmware Security Testing Methodology"
- OWASP "Mobile Security Testing Guide"
- "IoT Pentesting Guide" by Aditya Gupta
- "IoT Penetration Testing Cookbook" by Aaron Guzman and Aditya Gupta
- "The IoT Hacker's Handbook" by Aditya Gupta
- "Practical IoT Hacking" by Fotios Chantzis, Ioannis Stais, Paulino Calderon, Evangelos Deirmentzoglou, and Beau Woods
- further sources are referenced in the respective test cases
We also like to thank our collaborators and supporters (see Project Collaborators and Acknowledgements)!

