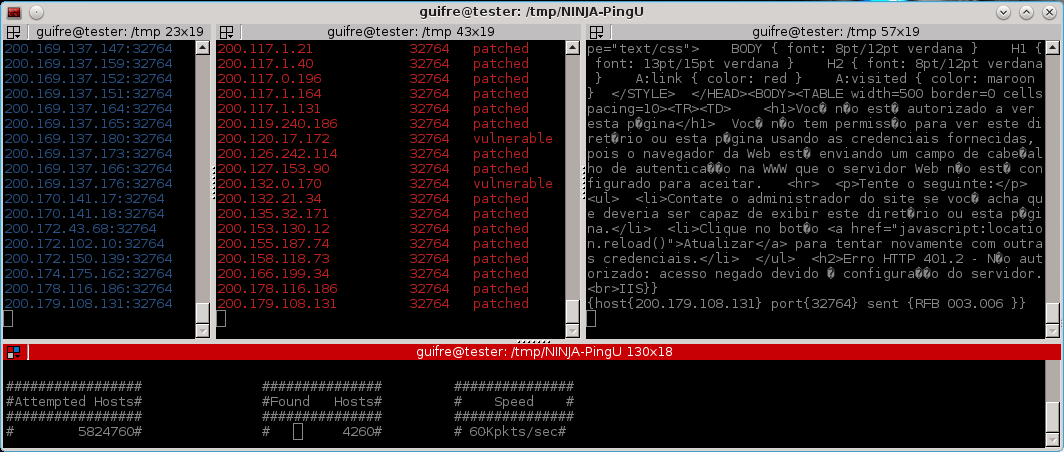
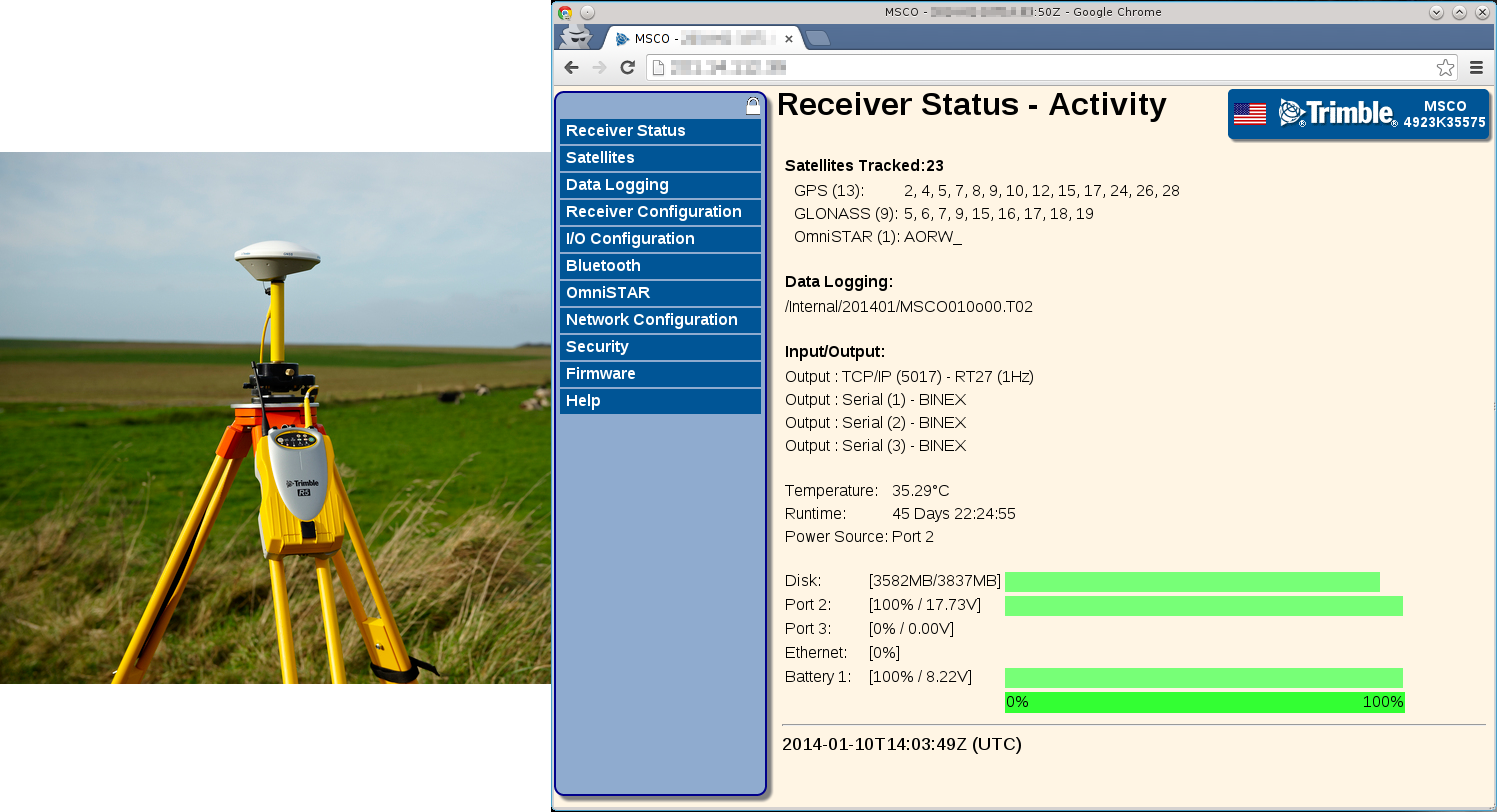
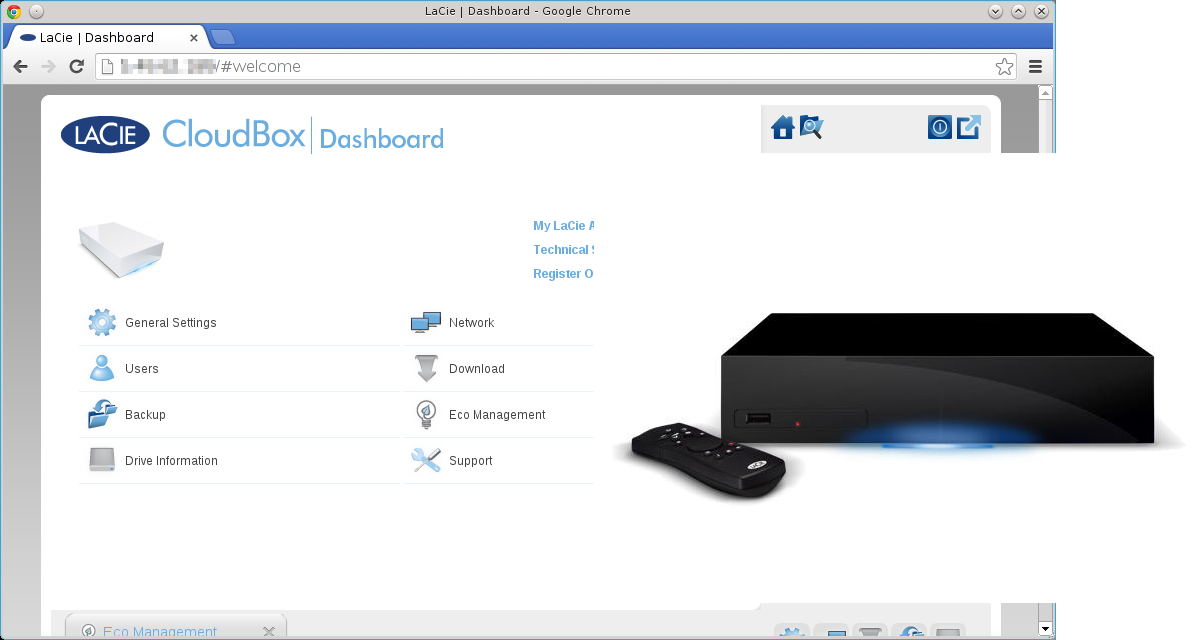
32764/TCP Backdoor Scanner Plugin
Millions of routers have been affected by a backdoor that gives full remote root access to the device. Backdoor32764 is the new plugin that identifies hosts affected by this backdoor.
The plugin is already available in the NINJA PingU codebase. You can run this plugin as follows.
# ./bin/npingu -t 2 -p 32764 1.1.1.1-255.0.0.0 -m Backdoor32764Embedded Devices & Services Discoverage Plugin
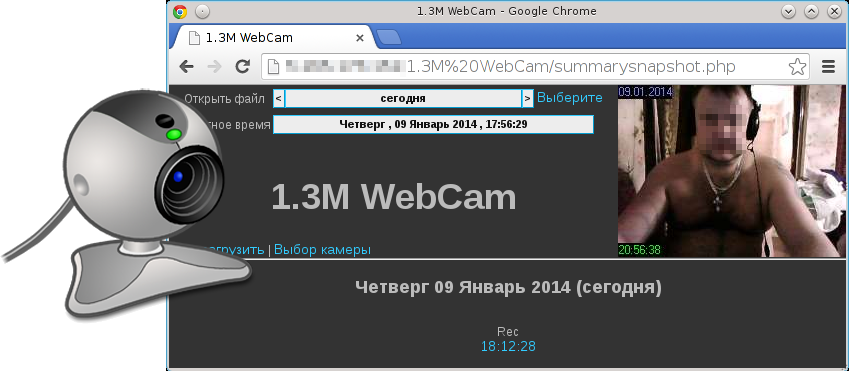
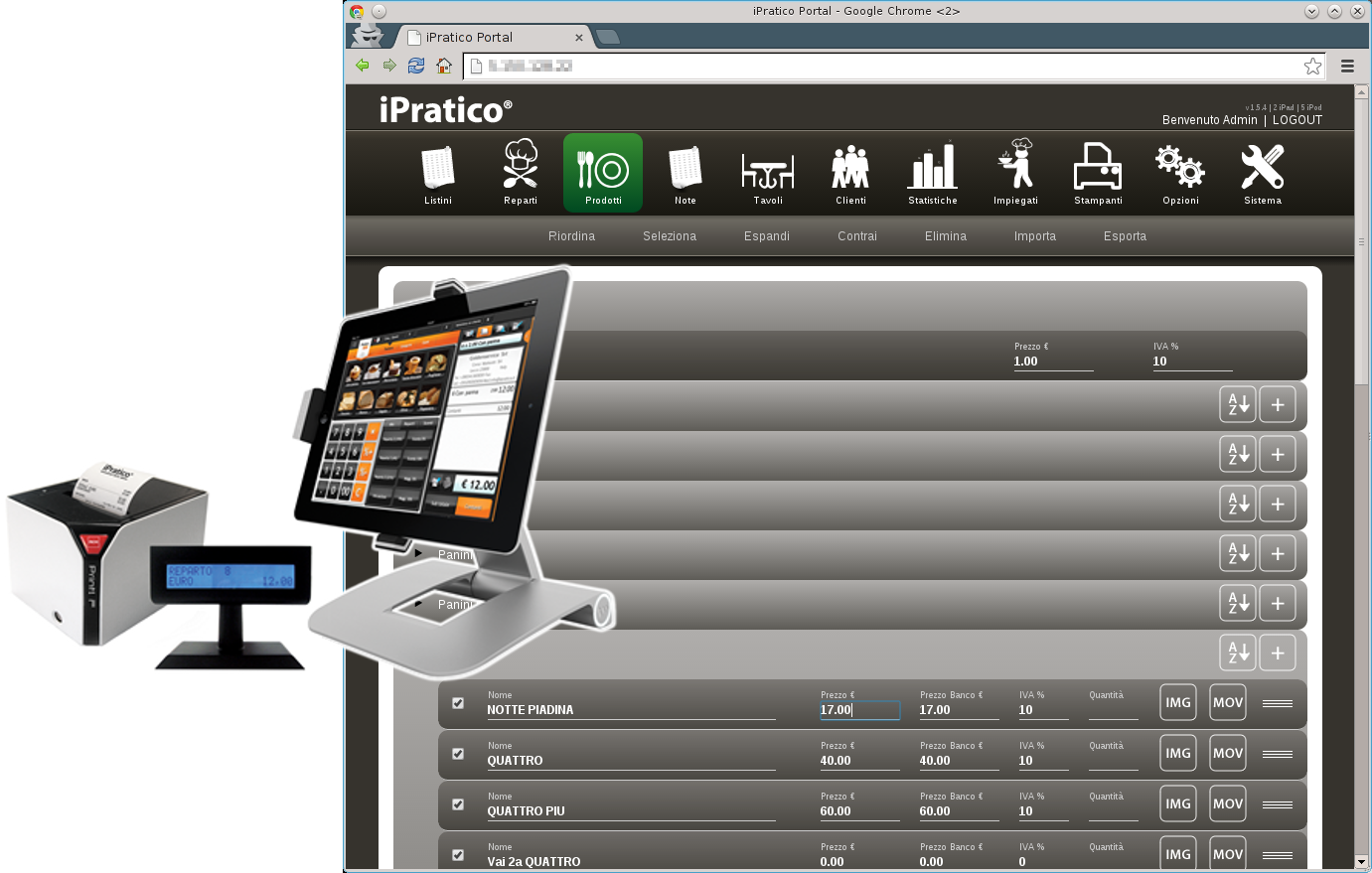
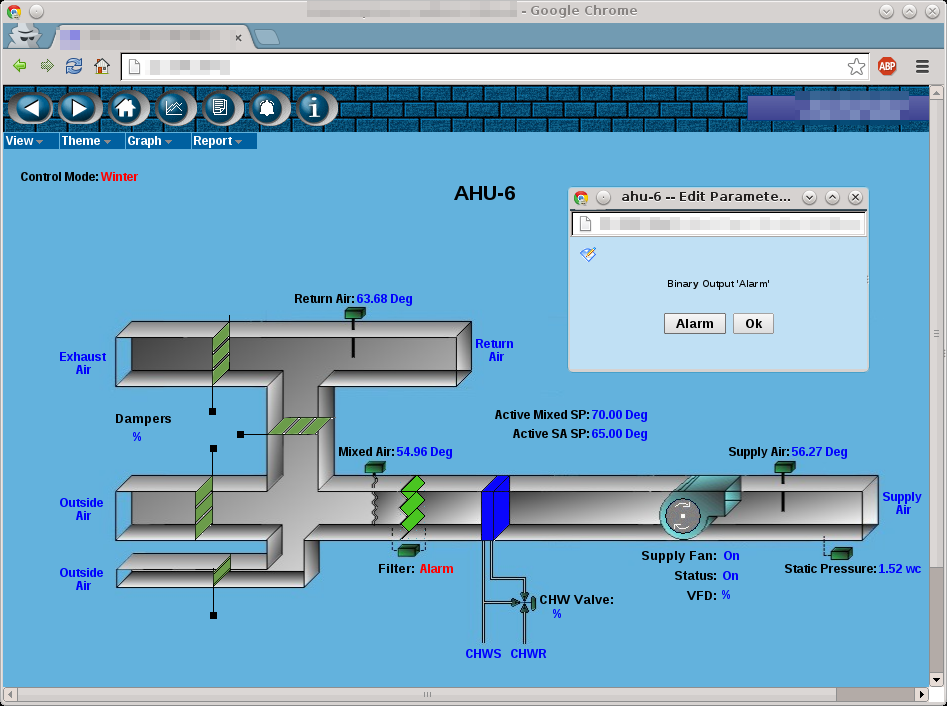
Recently, Bruce Schneier wrote about the security risks of embedded systems. To perform a simple experiment, I wrote a PoC plugin for NINJA PingU for services analysis and embedded devices discoverage.NINJA PingU comes out of the box with it.
The Service Discoverage plugin is targeted at performing a simple HTTP GET request to the port 80 of the targeted hosts and analyze Server banner response header. The plugin is open source and included in the v1.0 package. As NINJA PingU, the plugin is open source released in its codebase. This plugin can be run by using the following command.
# ./bin/npingu -t 5 -p 80 1.1.1.1-255.0.0.0 -m ServiceThe [-t 5] sets the number of spotter threads, the [-p 80] specifies the targeted port, [-m Service] loads the service and embedded device identification plugin. The following and several other devices are currently supported.