OWASP Security Champions Guide

Welcome to the home of the OWASP Security Champions Guide Project! Our goal is to create an open-source, vendor-neutral guidebook for AppSec professionals to help them build and improve their own successful Security Champion programs.
One size will not fit all – so this playbook is designed for you to pick and choose the elements your organization can adopt or leverage to create your own customized program. We will provide customizable artifacts that can be used to start or improve your program. It doesn’t stop there! As your program matures, the playbook will provide you with next steps and new factors for consideration to further empower your program and your champions.
To make this happen, our project team is interviewing security leaders, program coordinators, and security champions to establish what makes a successful program. Participants represent a range of company sizes, industries, geographies, and also different levels of security program maturity. We want to know what works, what doesn’t work, what promotes success, and what leads to failure.
We are looking for more participants to take part in this exciting project. Whatever your experience of Security Champions programs – good or bad – we want to hear from you! Especially if you are/have been:
- A security champion
- A program leader
- A CISO or executive in an organization with experience of Security Champions programs
Watch our latest project update here (11 minutes).
We’d love to hear your feedback and ideas. Check out the ‘Get Involved’ tab for more details.
The OWASP Security Champions Manifesto is a set of guiding principles crucial to any successful program.
The principles have been drawn from an initial series of in-depth interviews with Application Security leaders from across the globe as part of our wider goal to provide a comprehensive Security Champions playbook.
Go to the ‘Principles’ tab to find out more about these key principles and how to put them into practice.
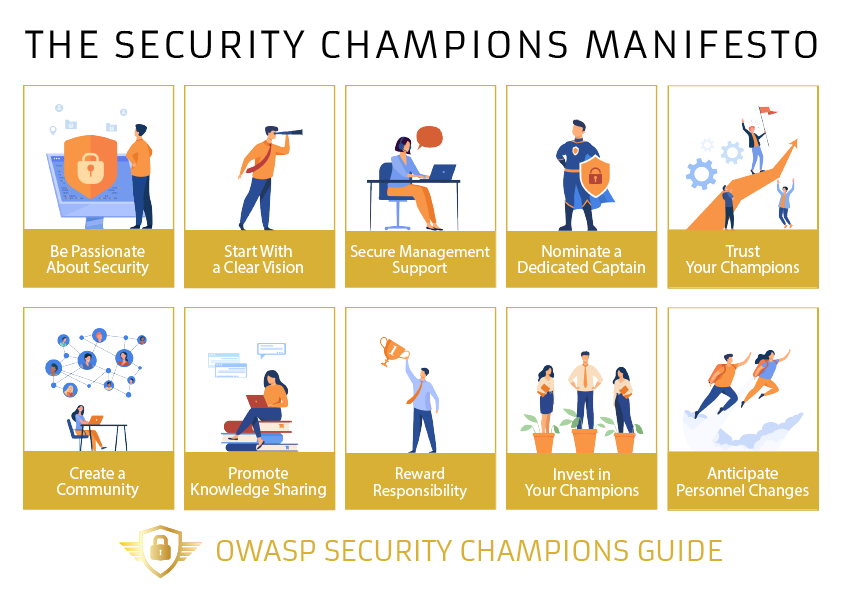
The Ten Key Principles for a Successful Security Champions Program
- Be passionate about security
- Start with a clear vision for your program
- Secure management support
- Nominate a dedicated captain
- Trust your champions
- Create a community
- Promote knowledge sharing
- Reward responsibility
- Invest in your champions
- Anticipate personnel changes
Prefer a visual? Download your copy of our principles infographic
The Ten Key Principles for a Successful Security Champions Program
- Be passionate about security
- Start with a clear vision for your program
- Secure management support
- Nominate a dedicated captain
- Trust your champions
- Create a community
- Promote knowledge sharing
- Reward responsibility
- Invest in your champions
- Anticipate personnel changes
![]()
1. Be Passionate About Security
What
Ensure the people involved in your security champion program are passionate about security. This passion helps to drive the program further and boost the security culture.
Why
Being passionate about security is crucial because it creates a mindset where security is not just a compliance requirement, but a fundamental part of how an organization operates. When employees are passionate about security, they are more likely to take ownership of security issues, be proactive about identifying potential risks, and advocate for security best practices throughout the organization.
How
Promote security top down and on all levels within your organization. Show security is taken seriously by management and is a key element of the DNA of the company. Then explain the importance of the security champions program within your organization. It should be clear what the program brings and what is expected of the people involved. The employees with passion for security should naturally be attracted to the program and raise their voice. Start with recruiting those volunteers and avoid assigning security champions when possible.
Be sure to enable passionate champions and invest in keeping them onboard. Trigger their curiosity and offer opportunities to keep on growing no matter what level they are on. Ideally, they also drive the program forward and make sure it covers their needs.
Don’t limit yourself to internal recruitment. Highlight the importance of security in your vacancies to attract passionate people that can boost the security culture. Ask candidates about their security experience and see if you can find that spark.
There are lots of opportunities to spark the passion of security champions. This checklist can be used to discover possible touch points and opportunities to do so.
![]()
2. Start with a clear vision for your program
What
A vision is defined as, “the act of power of imagination.” When you apply vision to the future, you can create a mental picture that can be used to direct your and your organization’s actions toward achieving security. A vision of security champions program serves as a guide in achieving security in your organization and can be used to provide a sense of purpose for IT engineers doing security.
Why
Having a vision is critical for your decision-making and the long-term success of your program. It gives your program purpose, and clearly articulates the ‘why’ and ‘what’ that you want to see happen and the change you want to achieve. Without a clear end goal or destination from the outset, it will be difficult to create meaningful goals and strategies and make effective decisions.
There are several angles for defining a vision for security champions. The most common angle is that of democratizing security knowledge in the development teams, removing dependencies on the central security team, and governing security in development teams.
How
A successful vision must be:
- Imaginable:
Convey a clear picture of what the future will look like. Translating this to your security champions program, you can consider drawing a security operating model with the roles and responsibilities of the security champions, dev(ops) engineers, IT Leads, Product Owner, and security organizations. - Desirable:
Appeal to the long-term interest of those who have a stake in the Enterprise. Translating this to your security champions program, you should consider describing the benefits of embedding security in the development team through a security champion, with mandate, knowledge, and skills to do security. - Feasible:
Describe realistic and attainable goals. For your security champions program include goals like “hours spent on security by the champion”, “training objectives of the champion”, ” the number of security champions meet-ups”, “the decrease of security risk”, etc. - Focused:
The vision should be clear enough to provide guidance in decision-making. What are the boundaries of security champions, what are commitments towards the program by senior management and what are expectations towards security champions? Is the scope of security champions to secure the entire enterprise? What is their role within the development team? What is their role compared to that of the Security Organization? - Communicable:
A vision is easy to communicate and can be explained quickly. Don’t write several pages of vision. A picture showing how security champions are enabling your goals in security and IT development will go a long way.
Please note that it is not advised to create your vision in isolation. By involving as many key stakeholders as possible, you’ll enable people to take greater ownership of the vision and increase commitment. Think about IT Leads, POs, senior developers, and security leaders to be part of this vision creation process. Once the vision is in a good draft, give it a try by explaining and selling to within your organization (senior management, developer community etc).
![]()
3. Secure management support
What
Ensure your security champion program is recognized as a formal program with a set purpose within your organization. This is achieved when you secure management support for the program.
Why
A successful security champions program brings unmatchable security benefits to the table. It scales your security mindset and your security organization to the IT Department. Security Champions means that IT engineers are championing security. Doing so requires the IT department and other relevant departments to spend time, effort, and budget to create, nurture and enable the security champions. And this priority will conflict with other IT and Business priorities. Out of experience, we know that when priorities conflict, formalized priorities win the battle. Even the most passionate security champion will struggle to prioritize security over the expected workload. This can lead to frustrations within your security champions and will harm your security champions program.
That is WHY we strongly advise securing management support for your security champion program. This makes the program a formalized priority for the IT Department and thus for the security champions. Security Champions can spend the needed time to improve security without the constant distraction of explaining to IT Leads, Product Owners, and middle management why time is spent on security activities.
How
Setting up a Security Champion program requires a thorough analysis of the stakeholders to get the program approved and supported. The Head of IT, to whom the security champions report, is a key stakeholder. This can be the IT department doing Application Development, the IT Department doing Infrastructure Development, or both. Besides the Head of IT, if there is a Security or CISO department, management from that department is also a stakeholder as they set the direction of security and the Security organization. There are views that Security Champions are an extension of that Security Organization. Therefore, the manager of the Security Organization is a key stakeholder in securing management support for your security champions program. Another dimension to consider is when your vision of the security champion program states that being a security champion should be included in the job description of IT Engineers. It is advised to identify HR as a stakeholder.
Once the right stakeholders are identified, it is advised to understand what is essential for them and build your security champion program case around them. For the Head of IT, this would be in the direction of utilizing IT resources optimally, delivering IT fast and with adequate security/risk levels. For the Security Organization (CISO), what makes them tick is that security processes, expectations, and governance are embedded in the champion’s model and a clear articulation of the benefits of having such a Security Champions program on top of the existing organization. Per stakeholders, the benefits should be articulated, including addressing the potential risks they see for their objectives.
Finally, the proposal of the program should be approved by each identified stakeholder, making the program a formal program.
Please see this artifact used by a financial company (bank) to build its case for formalizing the security champion program.
(p.s. In the included artifacts, clear disclaimers are included of the organization’s context and why re-consideration is needed when copying and pasting the model to the user’s organization).
![]()
4. Nominate a dedicated captain
What
Ensure you have a dedicated Captain to lead the development, implementation and continuous success of a Security Champions Program.
Why
Having a dedicated Captain for a Security Champions Program is important to ensure that the program has a clear strategy and roadmap and is well-organized on a continuous basis. Lack of a dedicated role for this task may lead to people doing it “on the side” while our experience and research shows that building and maintaining a Security Champion program is one that requires continuous attention.
Focus points for the dedicated Captain are:
-
Setting a clear strategy and roadmap for the Security Champions Program:
A dedicated Captain will create the strategy for the program and ensure this aligns with organizational goals and objectives. The dedicated captain furthermore can foster collaboration between security champions, other departments, and management to build a roadmap that is realistic and achievable. -
Obtaining management support:
A dedicated Captain will work with management to obtain support and resources (e.g. financial resources, time of security champions) for the program, which is essential for its success. The captain will serve as the face of the program towards (senior) management and report to management on its success. -
Building and maintaining a community:
A dedicated Captain will build and maintain a community of security champions within the organization. This community can help promote a culture of security awareness and best practices, and provide a valuable resource for sharing knowledge and experiences. The community, furthermore, once it has reached a level of maturity can take on independent security tasks, releasing some of the burden placed on dedicated security staff. -
Driving success:
A dedicated Captain can drive the overall success of the program by organizing events, providing guidance and support to security champions, and ensuring that the program is effectively promoted throughout the organization. -
Staying up-to-date on security practices:
A dedicated Captain can stay up-to-date on the latest information security practices and trends, and ensure that the Security Champions Program is aligned with industry best practices and incorporates this in the program roadmap. This ensures that the organization is well-prepared to handle any security threats that may arise.
How
The projects teams’ personal experience and interviews we have conducted with organizations that have Security Champions Programs have shown that leading a Security Champions program is a full-time job. In bigger organizations this may even require a small team. It is recommended to “nominate” or hire dedicated people that are passionate about this role and have the right skills set to drive it to ensure success. Having this as an “on the side job” takes away from the momentum and dedication needed to launch a successful program. Similarly, persons with security knowledge but lacking the right communication and organizational skills to drive such a program can be a factor in its lack of success.
This job vacancy can be used when looking to hire a dedicated Security Champion Captain.
![]()
5. Trust your champions
What
Trusting your champions is key to a successful Security Champions program. They are the eyes and ears of the organization and know exactly what their department’s security needs are.
Why
The Security Champions are the experts in their working area. A security team can never achieve that level of knowledge of the applications as they are not involved in the operational work. Using their expertise to set up the Security Champions program will increase the likelihood of success.
When making people responsible, it is key to allow them to understand and act according to the defined role. It will increase speed, but also increase involvement. Ideally the Security Champions co-own the program and strongly influence the direction and content. They can identify shortcomings and propose changes or give practical feedback on the matter.
Teams are more likely to trust their own champions as they are “one of their own” and not an “outsider” from the Security Team. They speak the same language and understand the context. This will lead to more effective communication, better collaboration and reduced resistance to change.
In summary, trust is the glue that holds a Security Champions Program together.
How
Trust is all about setting clear expectations. It should be clear to everyone involved what the Security Champions’ role is about and what their mandate is. Don’t be afraid to let your champions experiment with different approaches. Their lessons learned can be a valuable input to other departments, sharing is caring!
Give your Security Champions the mandate to make decisions on security within the risk appetite of your organization. By being in control and removing inefficiencies, they can add a lot of value to their teams and increase the security adoption & awareness. Do make sure they share their approach and reasoning to make sure the Security Champions can learn from each other and give constructive feedback.This way the organization can improve security related initiatives, decision making and processes..
Also involve the security champions in the processes of the core security team. Seek their input and opinions on security initiatives, policies, and practices to make them feel valued as active contributors. Use their feedback to improve the program, processes, and procedures.
Measure and showcase the impact that the Security Champions and the program make. Demonstrate how their efforts have positively influenced security outcomes, highlighting the value they bring to the organization. This will build up the Security Champions’ trustworthiness and boost morale.
![]()
6. Create a community
What
A community provides a platform for security champions to share knowledge, experiences, challenges, and best practices with each other. A community furthermore helps to foster a culture of security awareness, collaboration, and continuous learning among the security champions and their teams. A community can provide recognition, feedback, and support for the security champions.
Why
Creating an active and vibrant community of Security Champions is vital to the success of any Security Champions Program and provides an additional channel to scale the security program.
How
To create a community for a security champions program, the following should be considered:
-
Start by defining a clear purpose, goals, and scope of the community. This should be aligned with the vision of the security champion’s program (see pillar 2). What are the expected outcomes and benefits of the community? Define measurable success criteria and appoint a person to continuously monitor the status of success in the community. This can be the dedicated captain or one of his/her team members in case the security champions program is led by multiple individuals.
-
Define how the community will align with the organization’s security strategy and objectives. The dedicated captain and/or some champions will attend security strategy update sessions, or security executives will provide periodic updates in the security champions’ community on strategy and execution.
-
Establish regular communication and collaboration channels for the security champions to interact with each other and with the security team. This can include online forums, chat groups, mailing lists, social media platforms, shared workspaces that allow the security champions to ask questions, share ideas, discuss issues, provide feedback, etc.
-
Organize periodic events and activities for the security champions to engage with the community and learn from each other. This can include meetups, hackathons, workshops, presentations, demos, games, quizzes, etc. that showcase security projects, achievements, challenges, solutions, etc.
-
Recognize and reward the security champions for their contributions and achievements. This can include certificates, badges, trophies, prizes, opportunities to speak about security topics in the name of the organization, etc. to acknowledge and appreciate the security champions’ efforts and impact on improving security in the organization. Refer to pillar 8 for more details.
-
Provide group training opportunities to foster the sense of community and encourage security champions to learn from each other. A security champion with a lot of knowledge in a specific area can serve as a teacher to others in the community. They can develop (online) courses, workshops, webinars, podcasts, newsletters, blogs, etc for the security champions community. The dedicated captain has a big role in enabling this and providing the resources necessary to achieve this.
![]()
7. Promote knowledge sharing
What
Invest in the education of your Security Champions and encourage knowledge sharing within and outside the company.
Why
Security and technology are continuously evolving. Keeping up with developments requires a mindset of continuously learning. As Security Champions are the security front-runners in their teams and departments they are naturally interested in security related topics and want to learn more. They also know exactly what’s needed to improve their teams. By sharing their knowledge they can improve people, processes and technology. Any feedback during the knowledge sharing sessions can give valuable insights and strengthen the whole community. Additionally, it also ensures the security team is aware of the technology used within the organization and the (security) challenge it incorporates.
How
Promote a knowledge sharing culture, this is a mindset that values and rewards knowledge sharing among employees. Formal training programs can be rolled out using existing sharing and learning strategies within the company when available. Informal knowledge sharing via lunch sessions and pizza evenings can also be very valuable. Combine this with internal & external events to trigger the interest of your employees but make sure to rotate the speakers and topics to attract the biggest audience. Keep in mind that development teams are more likely to connect to the Security Champions that share something that’s relevant to daily activities.
Gamification can be used to introduce a competitive element in the training and sharing knowledge. Capture the flag events are a great way to trigger the curiosity of your development teams.
![]()
8. Reward responsibility
What
The principle of “Reward Responsibility” involves establishing a system within an organization to recognize and reward the efforts of Security Champions. This system is designed to encompass both tangible and intangible forms of recognition and rewards. It aims to acknowledge the contributions that Security Champions make in enhancing the security posture of the organization, including their dedication, innovations, and proactive measures in managing security-related issues.
Why
Acknowledging and rewarding Security Champions is crucial for several reasons. Firstly, it serves as a significant motivator, encouraging continued enthusiasm and dedication in their roles. When individuals see their efforts being recognized, they are more likely to take ownership and be proactive in their security responsibilities. Additionally, a reward system contributes to the overall effectiveness of the Security Champions program by fostering a positive and encouraging environment. It also plays a key role in talent retention within the program, as it demonstrates the organization’s appreciation and value for the commitment and efforts of its Security Champions.
How
To effectively implement this principle, organizations should develop a system that regularly recognizes the efforts of Security Champions. This could include setting up formal recognition programs, offering tangible rewards such as bonuses or professional development opportunities, and providing career advancement possibilities for effective champions. Additionally, regular feedback and expressions of appreciation are essential. Tailoring rewards to individual motivations is also key; some Champions might value public recognition, while others might appreciate personal development opportunities. The system should be designed to align with the organization’s culture and policies, ensuring that it is meaningful and sustainable. Please refer to The Star Model ™or the PDF for more information on the theory of reward systems.
Supporting Artifacts:
-
Recognition Certificate Templates:
Create customizable certificate templates to formally recognize the contributions of Security Champions. These certificates can be awarded for various achievements, like leading a successful security initiative, completing a significant amount of training, or significantly improving the security posture of a project. -
Security Champion of the Month/Quarter/Year Award:
Implement a periodic award program where Security Champions are nominated and selected for their outstanding contributions. This could include a physical trophy, certificate, or digital badge. -
Performance Dashboard:
Develop a dashboard that tracks and displays the contributions and achievements of each Security Champion. This could include metrics like issues resolved, training completed, or initiatives led. The dashboard can be used to identify candidates for rewards and recognition, in the form of gamification like security quizzes, etc. -
Personal Development Plan Template:
Offer a template for Security Champions to create their personal development plans. This plan can include their career goals, desired skills to acquire, and steps to achieve these goals, aligning with the organization’s opportunities for career advancement. -
Feedback and Endorsement Forms:
Create forms or systems for team members and managers to provide feedback or endorse Security Champions for their efforts. This feedback can be used as part of the evaluation process for awards and recognitions. -
Event Sponsorship Policy:
Create a policy or artifact detailing how Security Champions can be sponsored to attend relevant conferences, workshops, or training events. This not only rewards them but also contributes to their professional growth. -
Milestone Badges or Pins:
Design unique badges or pins that Security Champions can earn for reaching certain milestones or achievements. These can be physical items or digital badges for email signatures or internal profiles. Upon achieving specific badges, Security Champions can earn extended privileges like a mandate to review specific security policies, or a mandate to decide on specific risks or be part of security committees, etc.
![]()
9. Invest in your champions
What
Invest in the personal growth and development of your Security Champions.
Why
Security doesn’t come for free and requires investments. These investments also show the organization that security is taken seriously and boost the morale of the Security Champions. Without proper investments, the security program and security culture can quickly degrade.
Security Champions spend a lot of effort in learning, sharing and promoting security in the organization and play an important role in the security culture of a company. Don’t take the motivation of the Security Champions for granted. The organization should invest in them to make sure they feel appreciated and facilitate their development. This ensures the Security Champions community stays healthy and continues to drive the security program.
How
By formally allocating time for security activities the Security Champions can combine security work with their other responsibilities. This investment will increase the quality and reduce the amount of rework and incidents.
Allocate budget for webinars, conferences and training to ensure Security Champions can develop and gain new knowledge. These new insights can uncover vulnerabilities and will most likely improve the quality and throughput time of the deliverables. Internal workshops, sessions, training and events are a great way to share knowledge within the organization and get new people excited for security.
Introduce job titles/specialized roles to give recognition to the Security Champions. Bonuses and promotion can be an additional incentive for employees to take security seriously and walk that extra mile.
![]()
10. Anticipate personnel changes
What
The field of information security staffing has undergone significant changes over the last decade. The increased reliance on technology has made Information security skills essential in many industries, leading to a high demand for information security talent and a lot of job opportunities. This high demand and abundance of opportunities has impacted the turn-over rate of staff significantly and companies find it harder to retain information security talent. Therefore, organizations need to anticipate these personnel changes in their organization and their security champions program as they are unavoidable.
Why
Placing too high of a demand on a limited number of individuals as Security Champions increases the risk of a Security Champions program failing when certain, key, individuals leave the organization or change role within the organization.. Organizations need to acknowledge that people will leave, and ensure this does not bring the continuity of their Security Champions program in danger.
How
In order to ensure consistency and continuity in the Security Champions the following, complementary, recommendations can be made:
-
Have a reasonable ratio of champions to developers (e.g. 1 champion per 25 developers for large organizations);
-
Implement a T-shaped model for DevOps engineers, this means personnel possess a solid foundation in both development and operations, while also having the ability to contribute to other areas such as security (or automation, testing, etc). Reward personnel financially for their “additional” skill. This is further highlighted in Principles 8 & 9.
-
Ensure it is an officially recognized position in the organization and align with HR to adapt the recruitment & selection process towards hiring Security Champions;
-
Run a continuous training and educations program for security champions, this enables new joiners to grow into the role of Security Champion;
-
Do not adopt the 1 Champion - 1 team model but group champions based on specialism or type of technology, e.g. have a pool of security champions with an expertise on container security or API Security and use them as a liaison and knowledge base of their specific topic. Create collaborative working groups where knowledge is actively transferred. When one security champion then leaves the organization the rest of the group is able to “absorb the blow” of this person leaving.
Get Involved
If you are running a Security Champions Program, or starting one, reach out! Let’s talk, see where we can help and most importantly: if you used anything from us, let us know if that worked for you!
It would be great to receive contributions in the form of (anonymized) presentations, program documents or whatever can be useful in achieving a certain principle.
If you have a platform where we can talk about our Security Champions Program and would like to offer a collaboration or publication, reach out too! This really helps drive the message.
Contact us on LinkedIn to get involved!
Updates
Follow us on LinkedIn to get instantly notified on news and publications!
