OWASP Vulnerability Management Guide

About Project
Vulnerability management is one of the most effective means of controlling cybersecurity risk. Yet, as indicated by the wave of massive data breaches and ransomware attacks, all too often organizations are compromised over missing patches and misconfigurations. Vulnerability management seeks to help organizations identify such weaknesses in its security posture so that they can be rectified before they are exploited by attackers. The OWASP Vulnerability Management Guide (OWASP VMG) project seeks to establish guidance on the best practices that organizations can use establish a vulnerability management program within their organization. The guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability identification/scanning phase, the reporting phase, and remediation phase.
The vulnerability management guide should help to breakdown vulnerability management process into a manageable repeatable cycles tailored to your organizational needs. Target audience: information security practitioners of all levels, IT professionals, and business leaders.
Who is this project for?
OWASP VMG is for technical and non-technical professionals who are on the front line of information security engineering and their managers.
Here is a self-assessment to determine whether you need a robust vulnerability management program or not. All answers are confidential ;-)
- What is the size of your organization?
- a. 0-999
- b. 1K-10K
- c. 10K-25K+
- d. I don’t know…
- Do you have a dedicated security team?
- a. No
- b. In the process of forming it
- c. Yes
- d. I don’t know.
- Are vulnerability scans required in compliance of:
- a. PCI-DSS
- b. ISO 27001
- c. NIST 800-53
- d. I don’t know!
- Which of these sharing services is your organization most likely to utilize?
- a. FTP
- b. SFTP
- c. HTTPS
- d. SMBv1
- When was last time you had a security incident?
- a. During the last three months
- b. During the last three weeks
- c. During the last three days
- d. I don’t KNOW!!!
Results
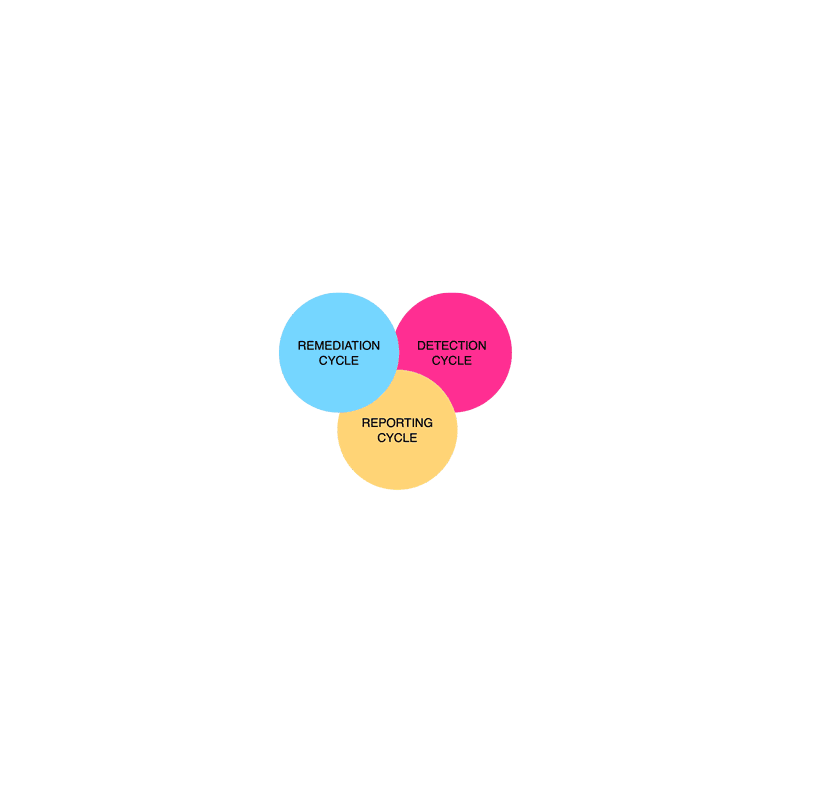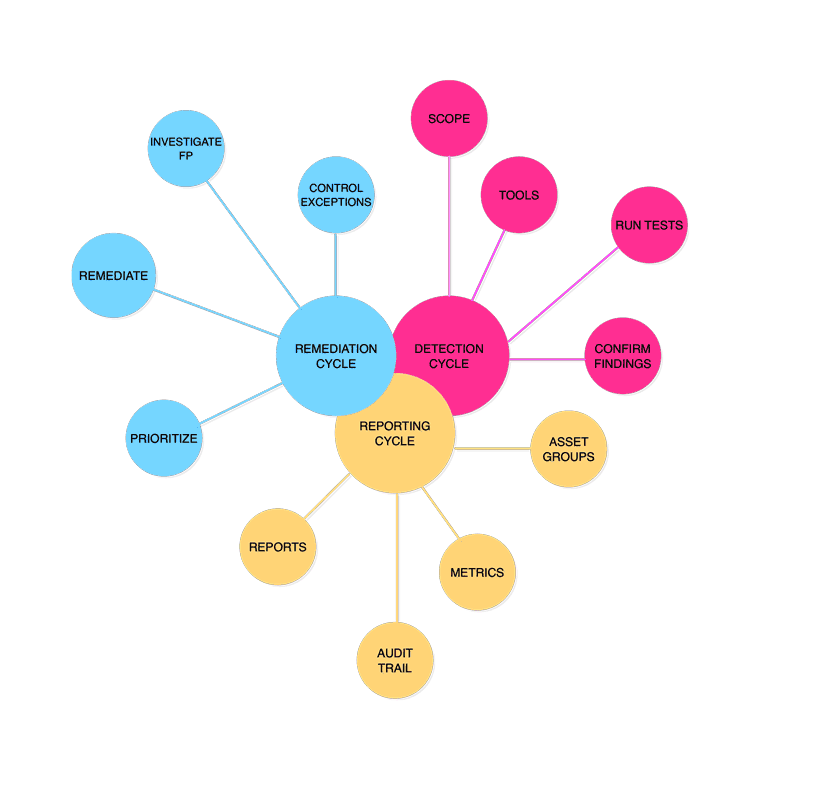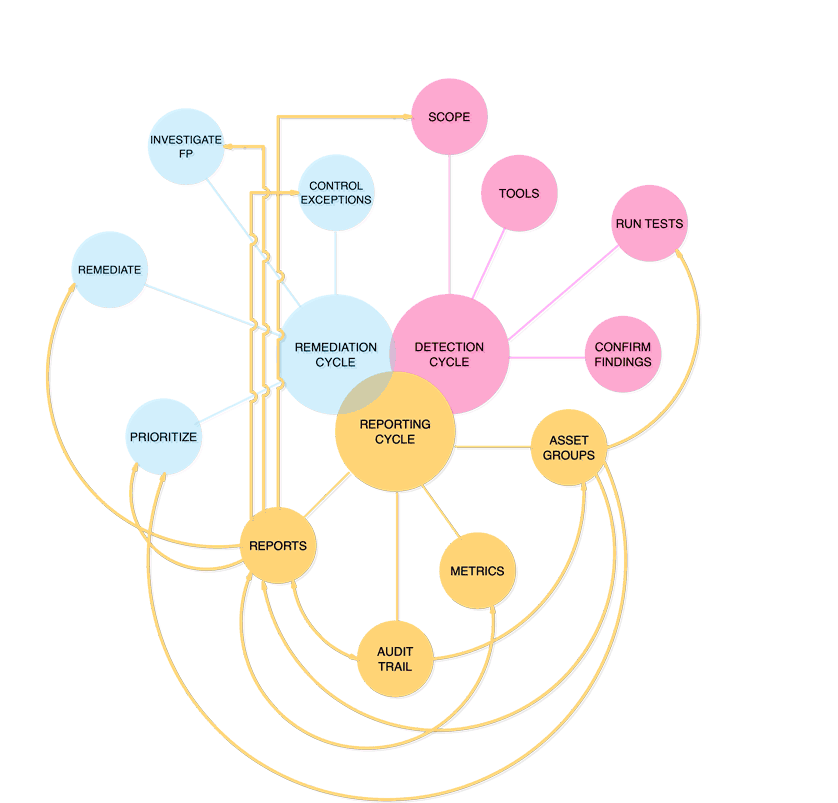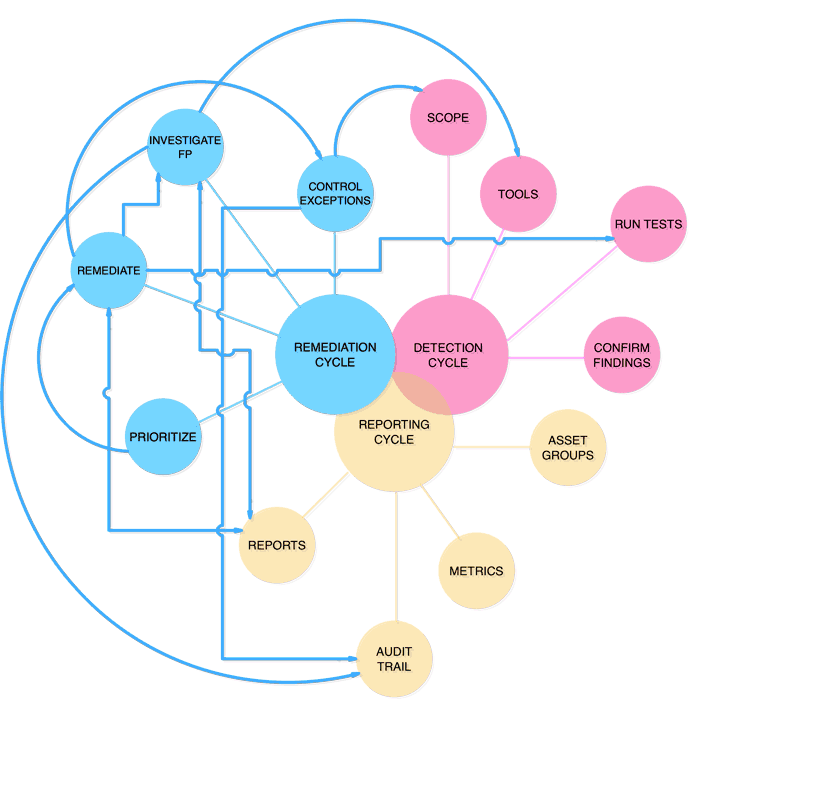
Vulnerability Management Cycle
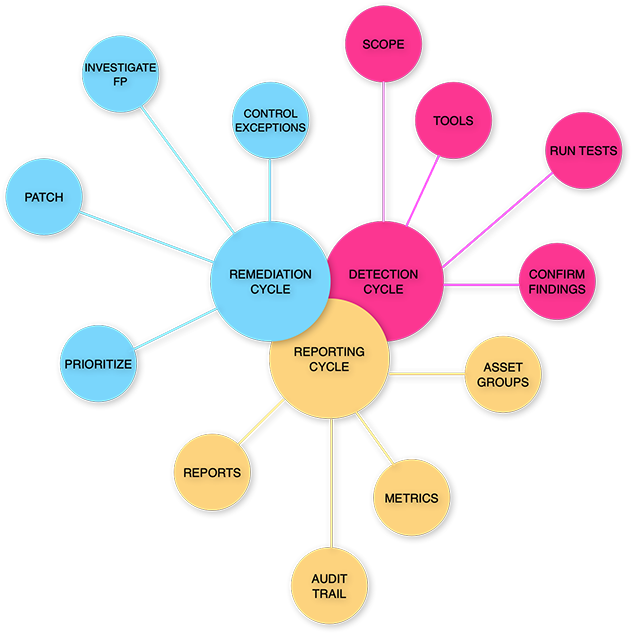
OWASP VMG TriCycle
Failures of vulnerability management programs are likely to result from failures of implementation caused by the common misconception that a working security scanner equals managing vulnerabilities in IT environments.
Vulnerability management cannot be outsourced to a single tool or even a set of very good tools that would seamlessly orchestrate a process around “some findings” and “some patches”.
The processes described in the guide involve decision making based on risk practices adopted by your organization. If you are tasked with rolling out a vulnerability management program – this guide will help you ask the right questions. If you are a manager or CISO, the guide should outline how a vulnerability management program can be integrated into your organization.
Regardless of your role, the purpose of the OWASP Vulnerability Management Guide is to explain how continuous and complex processes can be broken down into three essential parts, which we call cycles.
Where are we?
- OVMG Update coming soon
- OWASP VMG Working Group next scheduled session
- Written document
- Checklist (aka “bare bones”)
- A mind map “Vulnerability Management Cycle”
- Visual aid
Track the project
Join the cause
The simplest way to contribute to the OWASP Vulnerability Management Guide project is adopting it!
Please read the Guide and use “request feature” to ask your questions or something that would benefit you to speed up the implementation. Fork away the OVMG on GitHub.
How to collaborate
Please use the GitHub issue to post your ideas. OWASP is a highly dispersed team of InfoSec/IT professionals. Let’s utilize asynchronous communications to move OVMG along. Fill out the questionnaire in the Feature Request template by replacing the text in grey with your answers:
- Can you implement OWASP Vulnerability Management Guide at your place of work or business?
` Please state “yes” or “no’ and explain why. E.g.: “not applicable”, “I don’t work in InfoSec”, “too complicating”. […]`
- Is your feature request related to the OWASP VMG implementation? Please explain how.
` A clear and concise explanation of what the problem your request solves. […]`
- Please describe which of VMG cycles would host your addition? Detection, Reporting, Remediation.
` A clear and concise description how what you suggest could be plugged into the existing doc. […]`
- Describe alternatives you’ve considered
` A clear and concise description why alternative would NOT work.[…]`
- Did you read the OWASP VMG? What are your thoughts
` Your honest answer goes here.[…]`
Report Bugs
If you spot a typo or a missing link, please report to the GitHub issue. Much appreciated!
Code of Conduct
Important! You must adhere to the OWASP Code of Conduct.
Responsible Disclosure
Please allow some time to respond. Please check out OWASP Anti-Ransomware Guide Project and OWASP Secure Medical Device Deployment Standard.
Copyright lizfrenz 2023.