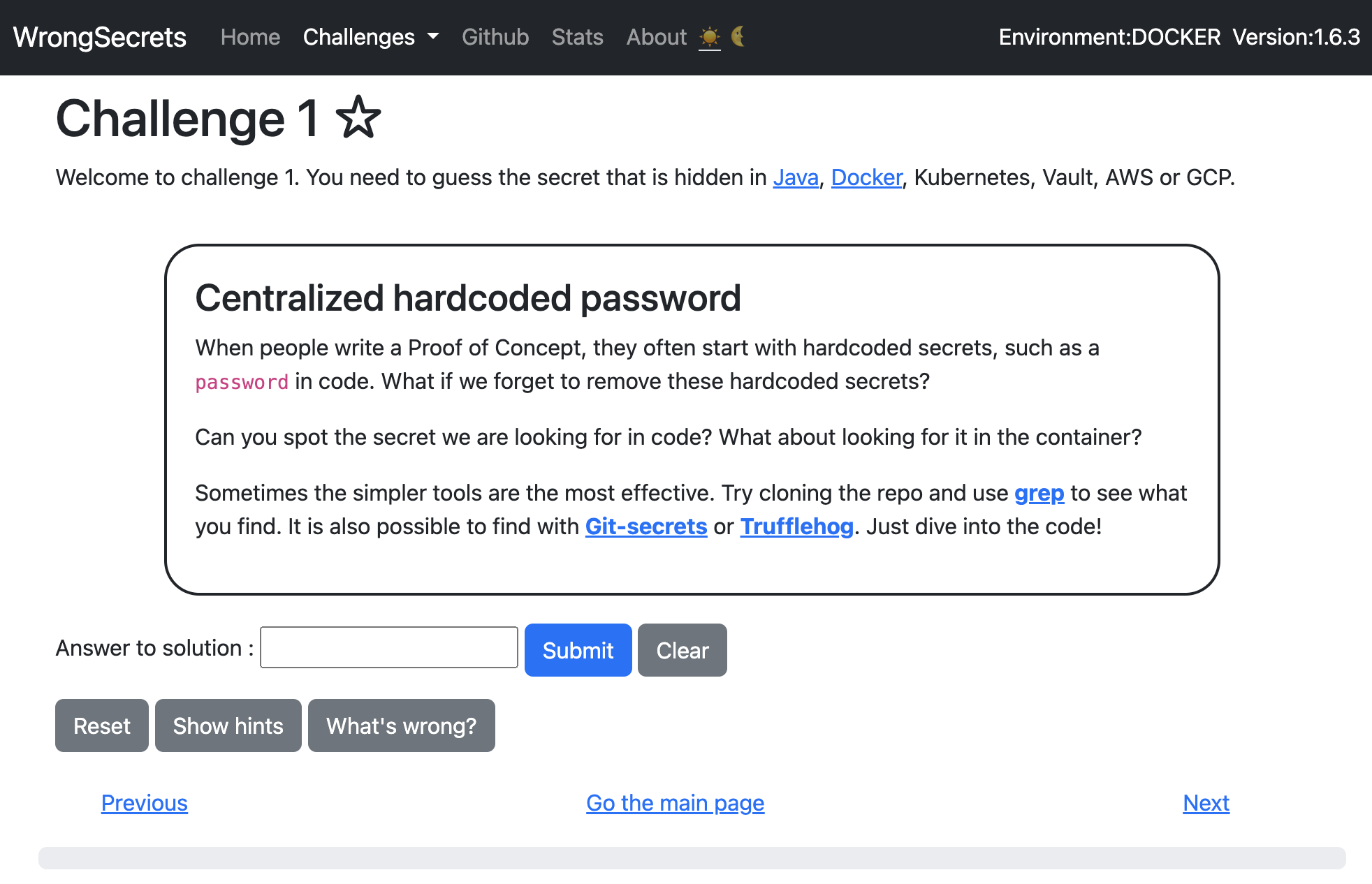
OWASP WrongSecrets
![]()
OWASP WrongSecrets is the first Secrets Management-focused vulnerable/p0wnable app! It can be used as a stand-alone game, as part of security trainings, awareness demos, as a test environment for secret detection tools, and bad practice detection tooling. It even has a supporting CTF platform to play the game in a larger group.
Want to give it a shot? Go to our Heroku demo environment
Description
WrongSecrets is based on Java, Docker, Terraform, and a bit of scripting fun. It contains more than 40 exercises with various wrongly stored or misconfigured secrets - which you need to find. Finding these secrets will
- Help you to look for secrets being misconfigured at your own environment, or target environments for bug bounties.
- Help you to re-evaluate your own secrets management practices as well.
Want to play?
There are multiple ways on how you can play/work with OWASP WrongSecrets. Want to play locally? Try
docker run -p 8080:8080 jeroenwillemsen/wrongsecrets:latest-no-vault
Otherwise, try one of the following online environments:
Or try to deploy it using free services:
Contributors
Leaders:
Top contributors:
Contributors:
- Nanne Baars @nbaars
- Marcin Nowak @drnow4u
- Rodolfo Cabral Neves @roddas
- Osama Magdy @osamamagdy
- Divyanshu Dev @Novice-expert
- Tibor Hercz @tiborhercz
- za @za
- Chris Elbring Jr. @neatzsche
- Diamond Rivero @diamant3
- Norbert Wolniak @nwolniak
- Adarsh A @adarsh-a-tw
- Shubham Patel @Shubham-Patel07
- Filip Chyla @fchyla
- Turjo Chowdhury @turjoc120
- Vineeth Jagadeesh @djvinnie
- Dmitry Litosh @Dlitosh
- Josh Grossman @tghosth
- alphasec @alphasecio
- CaduRoriz @CaduRoriz
- Madhu Akula @madhuakula
- Mike Woudenberg @mikewoudenberg
- Spyros @northdpole
- RubenAtBinx @RubenAtBinx
- Jeff Tong @Wind010
- Fern @f3rn0s
- Shlomo Zalman Heigh @szh
- Rick M @kingthorin
- Nicolas Humblot @nhumblot
- Danny Lloyd @dannylloyd
- Alex Bender @alex-bender
Testers:
- Dave van Stein @davevs
- Marcin Nowak @drnow4u
- Marc Chang Sing Pang @mchangsp
- Vineeth Jagadeesh @djvinnie
Special thanks:
- Madhu Akula @madhuakula @madhuakula
- Nanne Baars @nbaars @nbaars
- Björn Kimminich @bkimminich
- Dan Gora @devsecops
- Xiaolu Dai @saragluna
- Jonathan Giles @jonathanGiles
Sponsorships
We would like to thank the following parties for helping us out:
GitGuardian for their sponsorship which allows us to pay the bills for our cloud-accounts.
Jetbrains for licensing an instance of Intellij IDEA Ultimate edition to the project leads. We could not have been this fast with the development without it!
Docker for granting us their Docker Open Source Sponsored program.
1Password for granting us an open source license to 1Password for the secret detection testbed.
AWS for granting us AWS Open Source credits which we use to test our project and the Wrongsecrets CTF Party setup on AWS.
Individual supporters
-
Jeroen Willemsen
-
You want to appear on this list? Donate to OWASP here! 🤲
Licensing
This program is free software: You can redistribute it and/or modify it under the terms of the AGPLv3 License. OWASP WrongSecrets and any contributions are Copyright © by Jeroen Willemsen & the OWASP WrongSecrets contributors 2020-2024.
Want to help out?
You can help us in many ways:
- Star us on github: Star Wrongsecrets on Github
- Promote us using
.
- Promote us with a Blog, Vlog, Podcast, or presentation on a conference. Or use our materials to organize a CTF! If you do, let us know, so we can list your event or publication here on the webiste.
- Work with us on the project! Take a look at the Readme of the project, How to contribute, and the Github Issues. If you want to contribute to an issue: make sure it is not yet assigned to someone, comment on it with your intention, and then we can assign it to you.
- Sponsor our project! We will use the money for covering our cloud costs (building & maintaining the project in 3 clouds costs money). And soon we hope to be able to buy you some stickers if you do ;-).
Presentations about OWASP WrongSecrets
The project has been promoted at:
- AllDayDevOps: Our secrets management journey from Code to Vault
- Conf42 DevSecOps 2021: Secrets-management: challenges from code to cloud
- Club Cloud 2021: Securing your secrets in the cloud
- OWASP Dutch Chapter Meetup: Our Secrets Management Journey: From Code to Vault
- Open Security Summit: OWASP Wrong Secrets: project goals, under the hood, and where do we go from here?
- WrongSecrets demo - How not to store secrets with the project founder Jeroen Willemsen
- Security Journey: Jeroen Willemsen and Ben de Haan - Dirty little secrets
- Meetup OWASP Bay Area: OWASP WrongSecrets: how to NOT mange your secrets
- Code to Cloud Virtual Summit: Learn How to (Not) Use Secrets with OWASP WrongSecrets!
- Teqnation 2022 Utrecht
- Devops Pro Europe: Introducing OWASP WrongSecrets: How You Should NOT Handle Your Secrets
- OWASP Virtual Appsec Europe 2022: OWASP WrongSecrets: We have a secret for Everyone!
- Tweakers Developers Summit: OWASP WrongSecrets - waar je je applicatiegeheimen (niet) moet neerzetten
- OWASP Frankfurt #55 In-Person Event: Cloud Secrets,Cyber-Crime & Threat Modeling: Can’t you keep a secret? Learn Secrets Management with OWASP WrongSecrets by Dan Gora, OWASP Frankfurt
- OWASP Hamburg Stammtich
- DevSecOps Days 2022 Washington DC (Virtual): Learn How To (Not) Use Secrets With OWASP Wrong Secrets! and see the Youtube recording here
- AllDayDevOps - Learn how to (not) use secrets with OWASP WrongSecrets!
- Azure Cloud Security Group - Can’t You Keep a Secret ? Cloud Native Secrets Management with OWASP Wrong Secrets
- Azure Cloud Security Meetup: Cloud-Native Secrets Management with OWASP WrongSecrets by Dan Gora
- OWASP Benelux Days 2022 - CTF Kickoff with actual CTF info
- WeHackPurple: Don’t make the same mistakes we did: How you can do secrets management better with OWASP WrongSecrets
- Open Security Summit: OWASP WrongSecrets a journey into secrets management
- Open Security Summit: OWASP WrongSecrets: Define the future challenges togeter
- Cyberwisecon: OWASP WrongSecrets: How We Keep on Growing Our Open Source Project
- NLUUG: How to (not) Use Secrets with OWASP WrongSecrets recording from From 2:13
- Coverage on youtube: walkthrough by sec right
- Various Blogs: A blog by Gitguardian, Another blog by Gitguardian, Blogs by the author(s), A blog by Okteto, A blog by Nec, A blog from vineeth.dj.
- Various Podcasts: Application Security Podcast: Jeroen Willemsen & Ben de Haan – Dirty little secrets, Devsec for scale: Secrets Management Pt 1, Devsec for scale: Secrets Management Pt 2, Devsec for scale: Secrets Management Pt 3.
We would like to thank many people that have given a shoutout or a share about this project! Thank you for your forum-posts, blogs, and more!
Overview
The application can best be run as a Docker container as part of a K8s cluster. Some challenges are unique to specific public clouds (AWS, GCP, and Azure only for now).
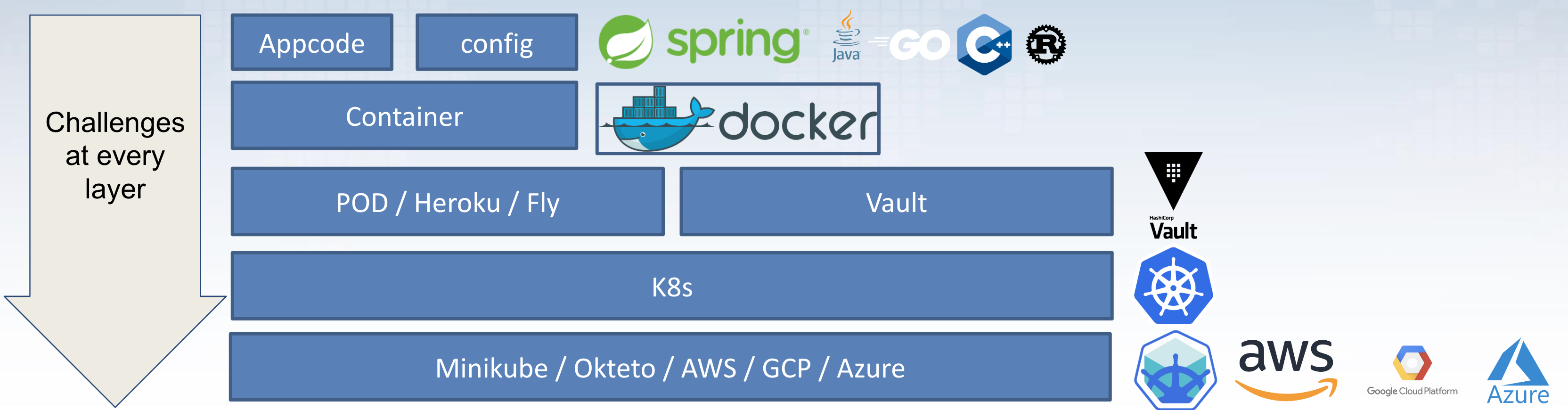
The overview above nicely shows which technologies are mostly used to build up the full application. Consult the GitHub repo readme for more information.
CTF
With just OWASP WrongSecrets
We support playing CTFs with OWASP WrongSecrets! Want to know more? Have a look at the Git repo README and the additional CTF documentation
With OWASP WrongSecrets-CTF-Party
Want to play OWASP WrongSecrets in a large group in CTF mode, but not go over all the hassle of setting up local copies of OWASP WrongSecrets? Here is OWASP WrongSecrets CTF Party! This is a fork of OWASP MultiJuicer, which is adapted to become a dynamic multi-tenant setup for doing a CTF together!
Note that we:
- have a Webtop integrated for each player
- have a WrongSecrets instance integrated for each player
- A working admin interface which can restart both or delete both (by deleting the full namespace)
- It can cleanup old & unused namespaces automatically.
You can currently play OWASP WrongSecrets CTF Party using:
- Any k8s setup that allows you to have multiple namespaces (including Minikube), by leveraging our helm charts.
- AWS, Azure, and GCP by using terraform which is part of the repo.
Special thanks
Special thanks to @commjoen, @madhuakula, @bendehaan, and @mikewoudenberg, and @osamamagdy for making this port a reality!
Wrongsecrets Desktop
Want to try out the secrets-hunting, but don’t want to install all the recommended tools? Try to use our WrongSecrets desktop.
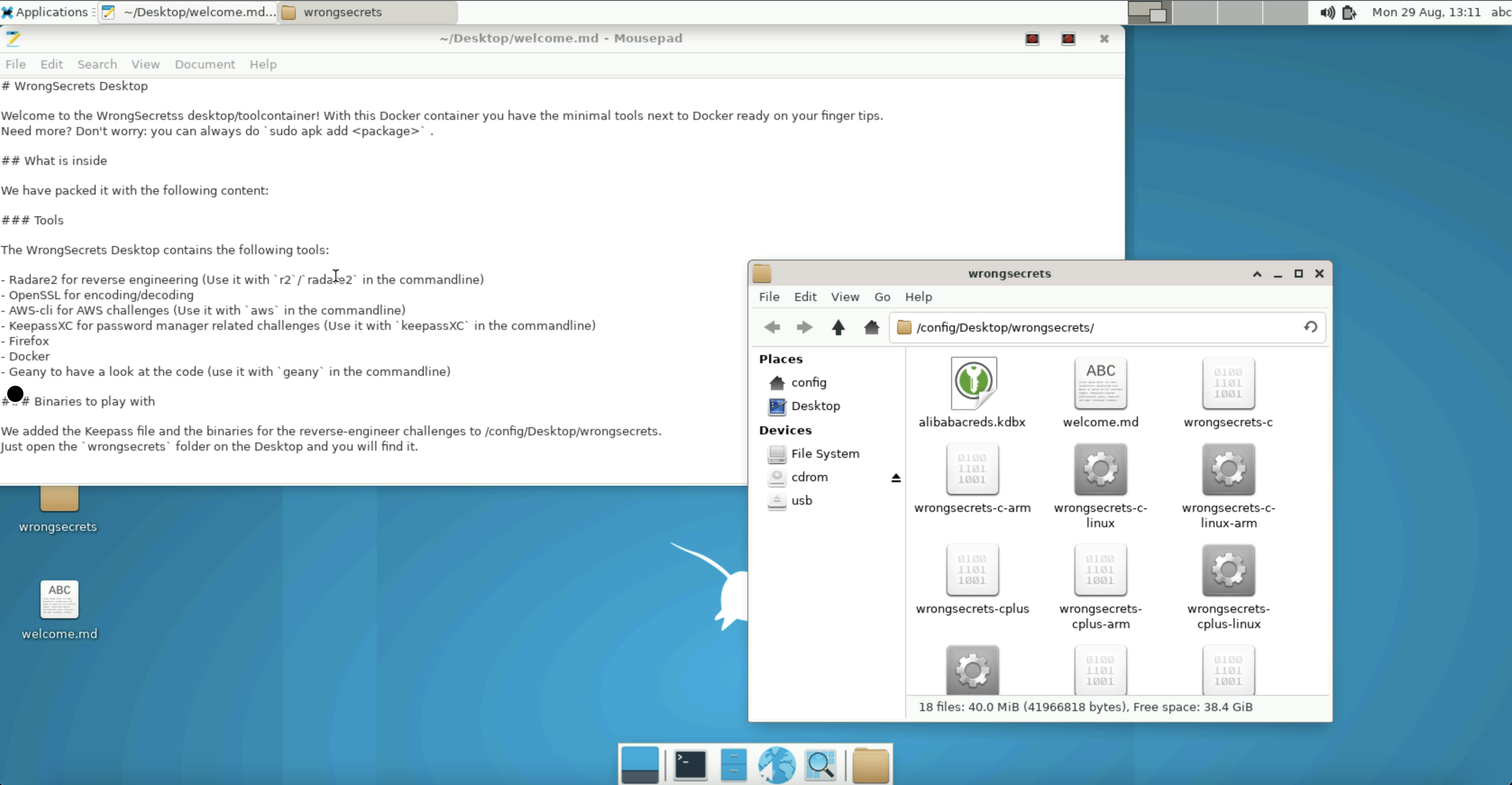
You can run all the tools and a desktop environment in a container by doing the following:
docker run -p 3000:3000 jeroenwillemsen/wrongsecrets-desktop:latest
and open a browser at http://localhost:3000. Want to know more? Checkout the Readme at the WrongSecrets github repo.
Creating Passwords
You can create various types of passwords. OWASP WrongSecrets has quite a few of them as an example. There are complex passwords, which you can easily create with tools like OpenSSL and/or password managers. There are short passphrases, which you can easily remember There are longer passphrases with a more extensive set of words involved.
Complex passwords
Complex passwords can be easily generated securely using tools like OpenSSL (using openssl rand 20 -base64) or a password manager. For instance, the generation of challenge 31’s password. The password (SGF2ZSBhIG5pY2UgZGF5) was obtained using random information generated through OpenSSL.
Of course, we need to reference the (in)famous XKCD on this topic.
Short passphrases
Short passphrases uses short combinations of words. These are easy to think of and easy to remember. The solution to challenge0 is a good example here. Here a short passphrase(The first answer) is used as a solution.
Longer passphrases
In other challenges we packed longer passphrases, which are still easy to remember, but do have a lot more entropy to them.
References
NIST Digital Identity Guidelines: https://pages.nist.gov/800-63-3/sp800-63b.html OWASP Authentication cheatsheet: https://cheatsheetseries.owasp.org/cheatsheets/Authentication_Cheat_Sheet.html



















