OWASP DevSecOps Guideline - v-0.2
Container Vulnerability Scanning
As containers become an almost ubiquitous method of packaging and deploying applications, the instances of malware have increased. Securing containers is now a top priority for DevOps engineers. Fortunately, a number of open source programs are available that scan containers and container images. Let’s look at five such tools.
What can Container Security Scanning do?
- Detect insecure containers
- Detect outdated libraries
- Detect incorrectly configured containers
- Detect outdated operating system
- Detect compliance validations
- Suggest best practices
Issues with Container Security Scanner
- Level of depth depends on tool being used, So the results that you’ll get are very dependent on the type of tool you choose.
- Easy to go “too far” with configuration, there are tools where you can configure so much different settings, that it’s easy to jump overboard.
- The scan results will lead to actionable events?
Where and When to use Container Scanner?
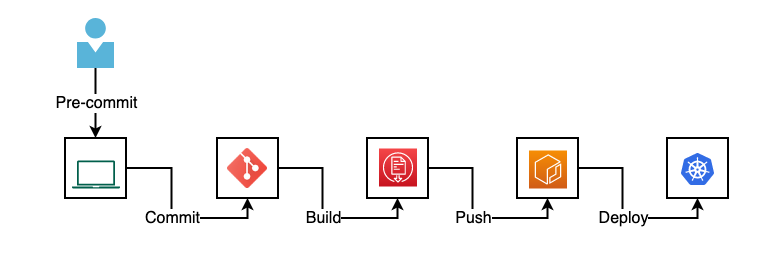
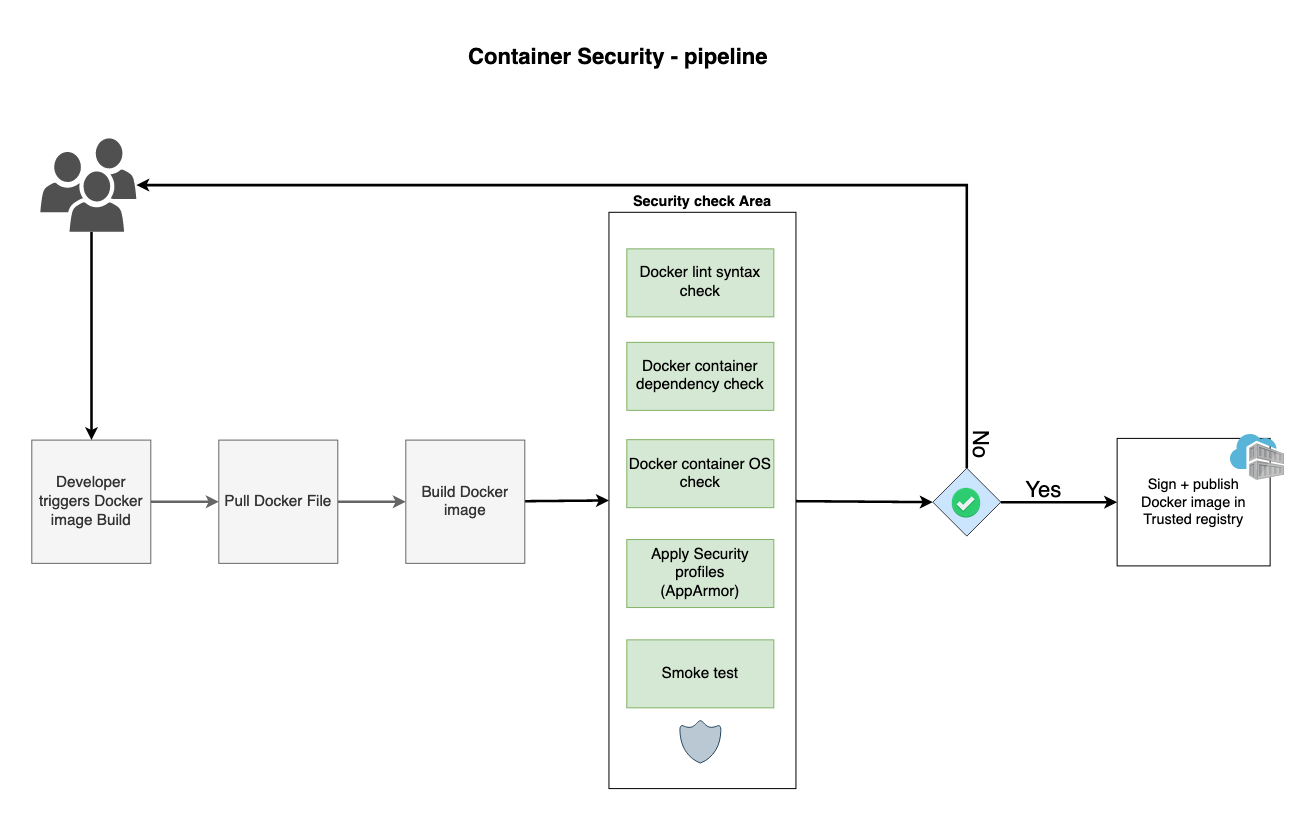
You can use it at the build phase when you’re actually building for instance a Dockerfile and looking at the resulting image that you’re creating. Another location to perform container scanning would be when you push a container to the registry or when you pull a container from a registry. However, a good approach is scanning before pushing into a trusted container registry then you can say we have a container registry with a scanned version of all images and for deploying in production you can pull from this trusted container registry. (Plase take look into the following image)
Tools:
- Clair - Vulnerability Static Analysis for Containers
- Anchore - Open-source project for deep analysis of docker images
- Dagda - A tool to perform static analysis of known vulnerabilities, trojans, viruses, malware & other malicious threats in docker images/containers and to monitor the docker daemon and running docker containers for detecting anomalous activities
- Falco - Falco, the cloud-native runtime security project, is the de facto Kubernetes threat detection engine
- Harbor - Harbor is an open source registry that secures artifacts with policies and role-based access control, ensures images are scanned and free from vulnerabilities, and signs images as trusted.
- Trivy - Trivy is a simple and comprehensive vulnerability/misconfiguration scanner for containers and other artifacts.