OWASP Core Business Application Security
OWASP CBAS Project Structure
Introduction
To allow organizations using enterprise business applications to determine an achievable, tailored-to approach defining actionable targets and measurable results, with the capability to scale by strengthening people, leveraging processes, and enhancing the use of tools. The Core Business Application Security (CBAS) project is designed to combine different industry standards and expertise from various security professionals to provide a comprehensive framework to align enterprise application security measures with the organization’s security strategy. As a result, a framework is created to improve the security governance of enterprise application technology.
Background
Core business applications or enterprise business applications are beneficial to organizations in several ways. Some of these benefits include:
- Combining different business processes under one solution
- Improving business performance
- Higher productivity by eliminating redundant processes
- Flexibility and mobility
- Easier collaboration between different organizational teams
- Centralized data
Even though there are numerous benefits that these solutions have, security threats have not decreased. Maintaining, implementing, and deploying security controls and/or information security standards around such solutions is still facing challenges. Some of these challenges include:
- Little to no understanding of the solutions in place
- Security professionals not involved in the initial phases of deploying and implementing such solutions
- Security controls being built after the solution is operational and functional; causing a blow back from business units
NO MONKEY Security Matrix
The NO MONKEY Security Matrix is used as a governance tool throughout the different projects under the CBAS-SAP. It combines elements of the security operational functions, defined by NIST, and IPAC model, defined by NO MONKEY, into a functional graph.
Benefits and the usage of the security matrix is listed under each project of the CBAS-SAP.
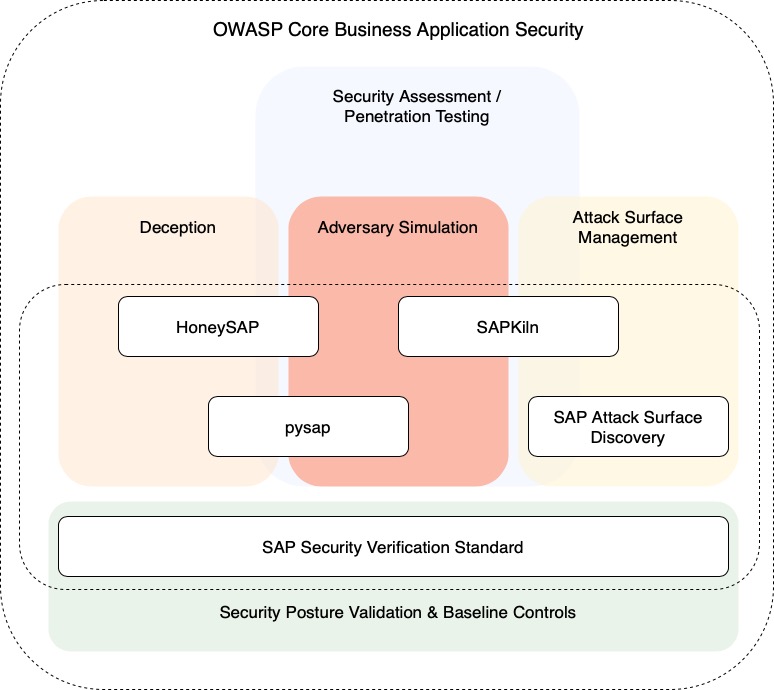
SAP Security Verification Standard
The CBAS - SAP Security Verification Standard (CBAS-SSVS) project allows organizations to determine their SAP security posture based on controls used to define a maturity level that organizations can maintain or adapt to. This enables organizations to plan and enhance their security mechanisms when protecting SAP resources.
HoneySAP: SAP low-interaction honeypot
HoneySAP is a low-interaction research-focused honeypot specific for SAP services. It’s aimed at learn the techniques and motivations behind attacks against SAP systems.
pysap - Python library for crafting SAP’s network protocols packets
SAP Netweaver and SAP HANA are technology platforms for building and integrating SAP business applications. Communication between components uses different network protocols and some services and tools make use of custom file formats as well. While some of them are standard and well-known protocols, others are proprietaries and public information is generally not available.
pysap is an open source Python 2 library that provides modules for crafting and sending packets using SAP’s NI, Diag, Enqueue, Router, MS, SNC, IGS, RFC and HDB protocols. In addition, support for creating and parsing different proprietary file formats is included. The modules are built on top of Scapy and are based on information acquired at researching the different protocols, file formats and services.
OWASP SAPKiln
SAPKiln is an open-source GUI tool designed to empower security researchers in conducting efficient auditing and penetration testing of SAP systems through SAP Logon/GUI (desktop application). It caters to both experienced SAP professionals and those unfamiliar with the SAP environment, as it streamlines the process of performing security checks with a user-friendly interface.
SAP Attack Surface Discovery
The project aims to help organizations and security professionals to identify and discover open SAP services through the use of different network scanning techniques. This allows individuals to further test these services for any potential threat that might affect SAP applications in their organizations.
News and Updates Channels
Anyone interested in supporting, contributing or giving feedback join us in our discord channel.
License

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
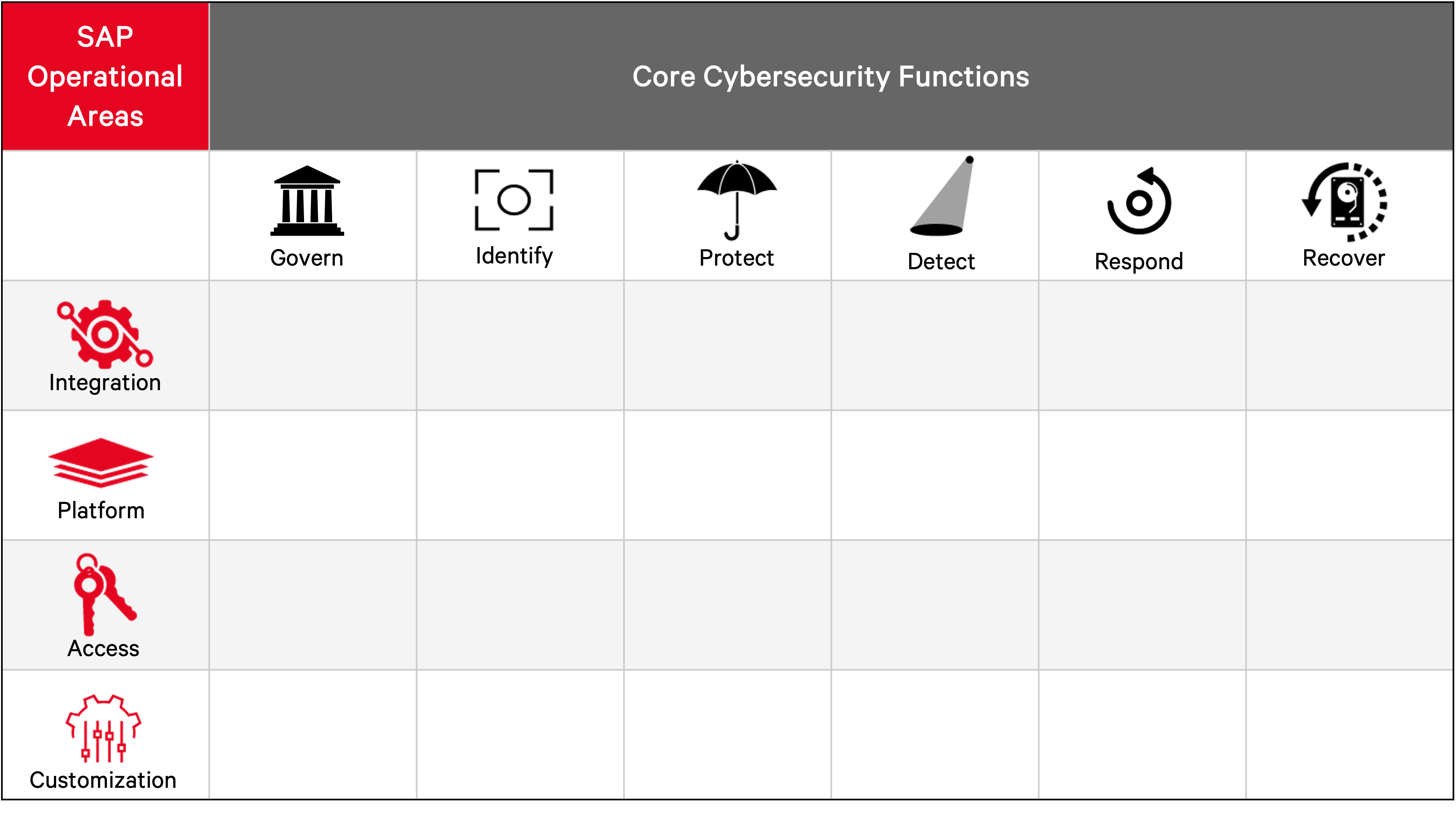
NO MONKEY Security Matrix
The NO MONKEY Security Matrix combines elements of the security operational functions, defined by NIST, and IPAC model, created by NO MONKEY and explained below, into a functional graph.

SAP Operational Areas
NO MONKEY has come up with the below four security areas to focus the security topics to a core business application. The areas are:
Integration: Focuses on different integration scenarios within systems and third-party tools integrating with a core business application environment, including proprietary and non-proprietary communication protocols and interfaces. Topics include secure architecture, security design, and general security operation concepts.
Platform: Focuses on vulnerabilities, hardening, and configuration of the core business applications. It includes reviewing security features and weaknesses in software operations, setup, and security management.
Access: Focuses on access control, user authorizations measures, and methodologies of SAP software.
Customization: Focuses on the customization of core business applications, including change management, custom code, business customizing, legacy interfaces, and add-ons.
Applicability
The Security Matrix serves as a starting point to:
- Visually show what areas within an organization can be improved; this can be achieved throughout the different projects released.
- Identify responsibility and knowledge gaps that are aligned to the areas of the Security Matrix within the Security Aptitude Assessment project
Below is a list of projects that benefit from the NO MONKEY Security Matrix:
SAP Security Verification Standard
The CBAS - SAP Security Verification Standard (SSVS) project allows organizations to determine their SAP security posture based on controls used to define a standard security baseline that organizations can maintain and adopt. This enables organizations to plan and enhance their security mechanisms when protecting SAP resources.
Whats In It For Me (WIIFM)
The project intends to be used by different professionals:
- SAP Security Experts
- non-SAP Security Experts
- Consultants
- Auditors
- Advisors
- The project helps operations, security, and audit teams assess, plan, and verify security controls that affect SAP implementations in their organizations.
- Helps organizations determine their maturity in protecting their SAP applications.
- Enables and supports organizations with implementing security controls that are required to protect their SAP applications.
Standard Definition
In our initial release, we want to create a security baseline every organization must maintain to secure SAP applications.
The initial release is derived from the below standards:
- SAP Security Baseline Template V2.4
- German Federal Office for Information Security - BSI 4.2 SAP ERP System
- German Federal Office for Information Security - BSI 4.6 SAP ABAP Programming
- SAP security white papers - used for critical areas missing in the security baseline template and BSI standards
- OWASP Application Security Verification Standard ASVS 2.0
- NO MONKEY Security Matrix
Controls
We aim to create controls in a structured, easy, and understandable way.
- Every control follows the same identification schema and structure
- Markdown language used for presenting the controls
- Excel tool to present maturity levels, risk areas represented by the NO MONKEY Security Matrix, and implementation status
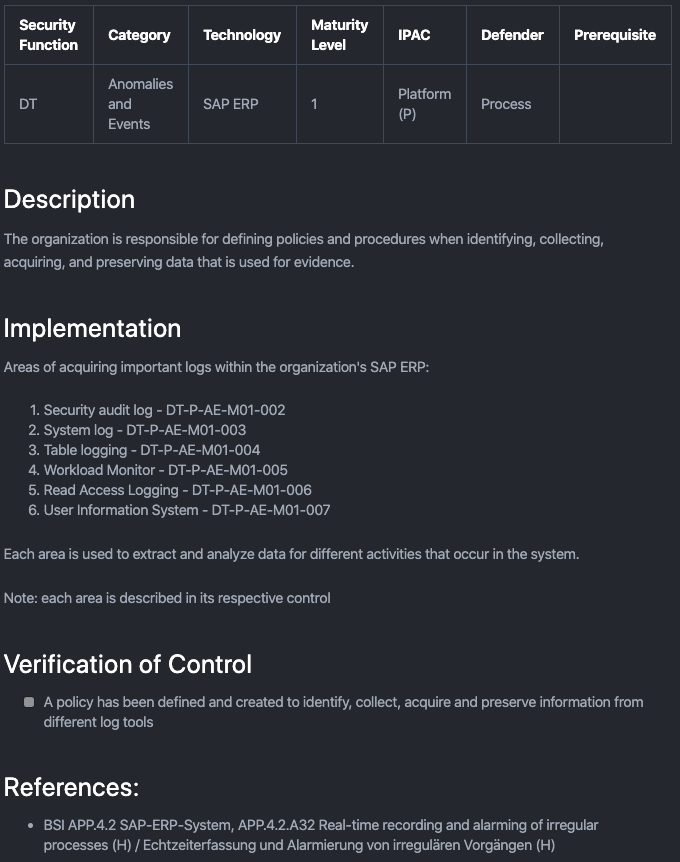
Control Header:
- NIST Security Function
- NIST Category
- IPAC Model
- SAP Technology
- Maturity Level
- Defender (People, Process, Technology)
- Control Prerequisite
Appendix A lists the acronyms used in either the control header or the naming convention for controls.
Control Structure:
- Description of the control
- Implementing the control
- Verification of the control
- References
Example:
SAP Attack Surface Discovery
[!WARNING] Make sure you have the appropriate permissions to actively scan and test applications. Without doing so, you might face legal implications
The project aims to help organizations and security professionals to identify and discover open SAP services through the use of different network scanning techniques. This allows individuals to further test these services for any potential threat that might affect SAP applications in their organizations.
OWASP CBAS project
Three areas within the NO MONKEY Security Matrix can benefit from the project:
- Identify – NIST Security Functions
- Detect - NIST Security Functions
- Integration – IPAC Model
Identify | Integration
When applied to a single organization, the results from the project can aid organizations to further concentrate their efforts in the IDENTIFY and INTEGRATION quadrant of the NO MONKEY Security Matrix.
Detect | Integration
Another potential area of benefit will be under the DETECT and INTEGRATION quadrant, this will allow organizations to automate their monitoring capabilities when it comes to publishing SAP application to the internet. If publishing these applications is not a requirement and have been done due to misconfiguration then the organization would be able to properly detect it.
More information can be found on the OWASP CBAS project Page
SAP Attack Surface Discovery Wiki
More information, benefits and details to each service can be found in the Wiki
Communication and Contribution
Anyone interested in supporting, contributing or giving feedback join us in our discord channel
We have also included a section about contribution in out Wiki, which can be found here
HoneySAP: SAP Low-interaction honeypot
Version 0.1.2.dev0 (XXX 2022)
Overview
HoneySAP is a low-interaction research-focused honeypot specific for SAP services. It’s aimed at learn the techniques and motivations behind attacks against SAP systems.
Features
- Low-interaction honeypot for SAP services
- YAML and JSON-based configuration
- Pluggable datastore backend
- Modular services system
- Modular feeds system
- Console logging
Installation
To install HoneySAP, simply download the sources and run:
$ python -m pip install .
A more complete guidance on how to install HoneySAP on different environments is provided in the documentation.
Documentation
Documentation is available at Read the Docs.
License
This tool is distributed under the GPLv2 license. Check the COPYING file for more details.
Authors
The tool was initially designed and developed by Martin Gallo while working at SecureAuth’s Innovation Labs team, with the help of many contributors. The code was then contributed by SecureAuth to the OWASP CBAS Project in October 2022.
Disclaimer
The spirit of this open source initiative is to help security researchers, and the community, speed up research and educational activities related to the implementation of networking protocols and stacks.
The information in this repository is for research and educational purposes and not meant to be used in production environments and/or as part of commercial products.
If you desire to use this code or some part of it for your own uses, we recommend applying proper security development life cycle and secure coding practices, as well as generate and track the respective indicators of compromise according to your needs.
pysap - Python library for crafting SAP’s network protocols packets
Version 0.1.20.dev0 (XXX 2022)
Overview
SAP Netweaver and SAP HANA are technology platforms for building and integrating SAP business applications. Communication between components uses different network protocols and some services and tools make use of custom file formats as well. While some of them are standard and well-known protocols, others are proprietaries and public information is generally not available.
pysap is an open source Python 2 library that provides modules for crafting and sending packets
using SAP’s NI, Diag, Enqueue, Router, MS, SNC, IGS, RFC and HDB protocols. In addition, support for creating and parsing different proprietary file formats is included. The modules are built on top of Scapy and are based on information acquired at researching the different protocols, file formats and services.
Features
-
Dissection and crafting of the following network protocols:
- SAP Network Interface (
NI) - SAP
Diag - SAP
Enqueue - SAP
Router - SAP Message Server (
MS) - SAP Secure Network Connection (
SNC) - SAP Internet Graphic Server (
IGS) - SAP Remote Function Call (
RFC) - SAP HANA SQL Command Network (
HDB)
- SAP Network Interface (
-
Client interfaces for handling the following file formats:
- SAP
SARarchive files - SAP Personal Security Environment (
PSE) files - SAP SSO Credential (
Credv2) files - SAP Secure Storage in File System (
SSFS) files
- SAP
-
Library implementing SAP’s
LZHandLZCcompression algorithms. -
Automatic compression/decompression of payloads with SAP’s algorithms.
-
Client, proxy and server classes implemented for some of the protocols.
-
Example scripts to illustrate the use of the different modules and protocols.
Installation
To install pysap simply run:
$ python -m pip install pysap
pysap is compatible and tested with Python 2.7. A Python 2/3 compatible version is in the workings but it’s not finalized yet.
Documentation
Documentation is available at Read the Docs.
License
This library is distributed under the GPLv2 license. Check the COPYING file for more details.
Authors
The tool was initially designed and developed by Martin Gallo while working at SecureAuth’s Innovation Labs team, with the help of many contributors. The code was then contributed by SecureAuth to the OWASP CBAS Project in October 2022.
News
- [September 2023] The SAP Internet Research project goes under a complete update and is now called the SAP Attack Surface Discovery
- [September 2023] The OWASP CBAS Roadmap is created to provide a clear view and direction of the different improvements and security areas that will be covered
- [August 2023] The OWASP SAPKiln project, lead by Alex Devassy, is added under the umbrella of the OWASP CBAS
- [August 2023] Alex Devassy joins the OWASP CBAS team
- [July 2023] Julian Petersohn contributes and takes lead on the SAP Internet Research project
- [July 2023] Julian Petersohn joins the OWASP CBAS team
- [October 2022] SecureAuth’s Innovation Labs donates the HoneySAP and Pysap projects to the OWASP CBAS
- [October 2022] Martin Gallo joins the leadership team
- [September 2020] Joris Van De Vis (@jvis) donates the SAP Internet Research project to the OWASP CBAS
- [June 2020] NO MONKEY donates the SAP Security Matrix to the OWASP CBAS
- [June 2020] OWASP CBAS created by Waseem Ajrab and Marco Hammel to provide a central location to address areas for SAP security
Events
COMING SOON
Roadmap

CBAS Supporters and Contributors
We are grateful for all our supporters and contributors that have spent a significant time working on the OWASP Core Business Application Security project.
We are continuously updating and improving the different parts of the project. All contributions are welcome. Get in touch with us to know more!
Supporters (Time and Donation) - Organizations
Organizations who have allowed contributors and/or donated a significant time and material on working on the different projects within the OWASP Core Business Application Security. Supporters contributing time and material will be evaluated at the sole discretion of the project leaders.
Supporters (Time and Donation) - Individuals
- Joris van de Vis - Protect4s - SAP Internet Research Project
Contributors
A live update of contributors can be found under each area of the OWASP Core Business Application Security project.
- SAP Security Verification Standard
- pySAP
- HoneySAP
- SAP Attack Surface Discovery
- SAPKiln
- SAP Security Aptitude assessment
CBAS Contribution Guidelines
We are grateful for all our supporters and contributors that are willing to spend time and effort on working on the OWASP Core Business Application Security projects.
Particpate in Dicussions
We’re using Discussions as a place to connect with other members of our community. We hope that you:
- Ask questions you’re wondering about
- Share ideas
- Engage with other community members
- Welcome others and are open-minded. Remember that this is a community we build together
Join our OWASP CBAS Discord or Slack Channel to stay up-to-date with any updates or news.
Contribution Steps
1. Create Issues
First create issues before opening any pull requests. Issues will be discussed for any missing requirements, content, duplications, or bugs.
Assignment will be done by project leaders.
2. Opening Pull Requests
Once you have opened a Pull Request, a reviewer will make sure all requirements are met and submitted for a merge. (refer to the Review page to learn more)
Becoming a Reviewer
COMING SOON





