OWASP VulnerableApp
![]()
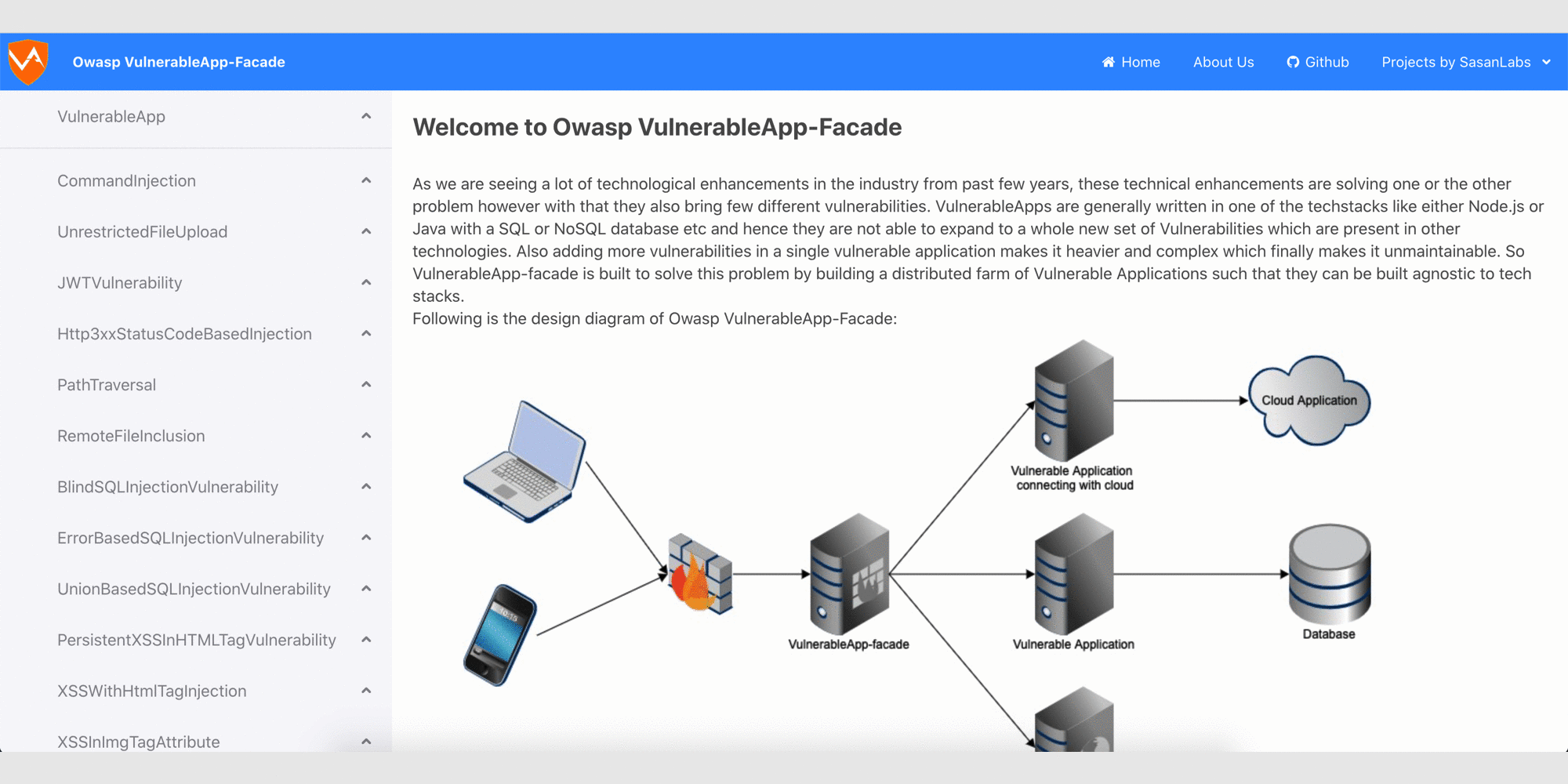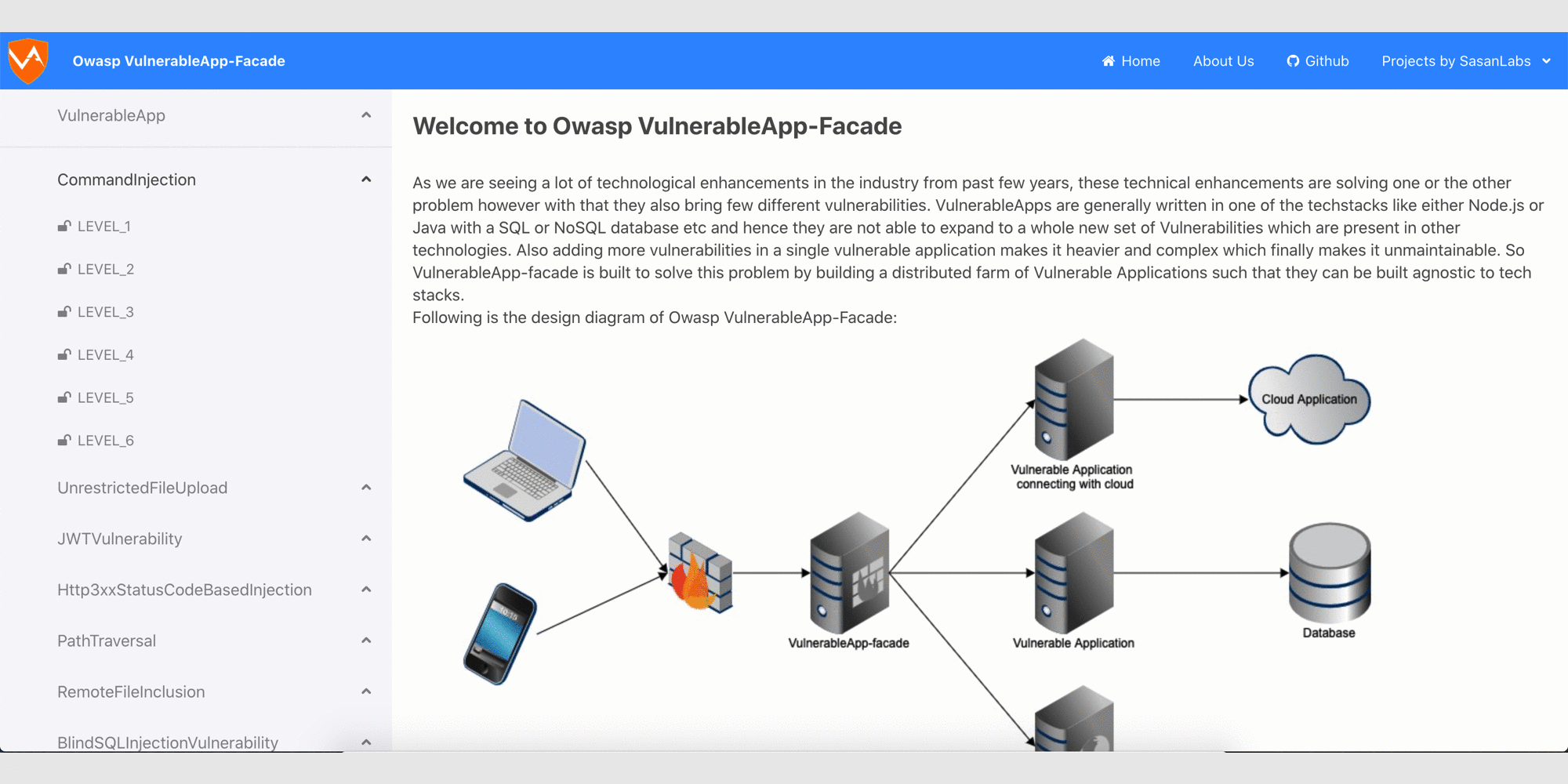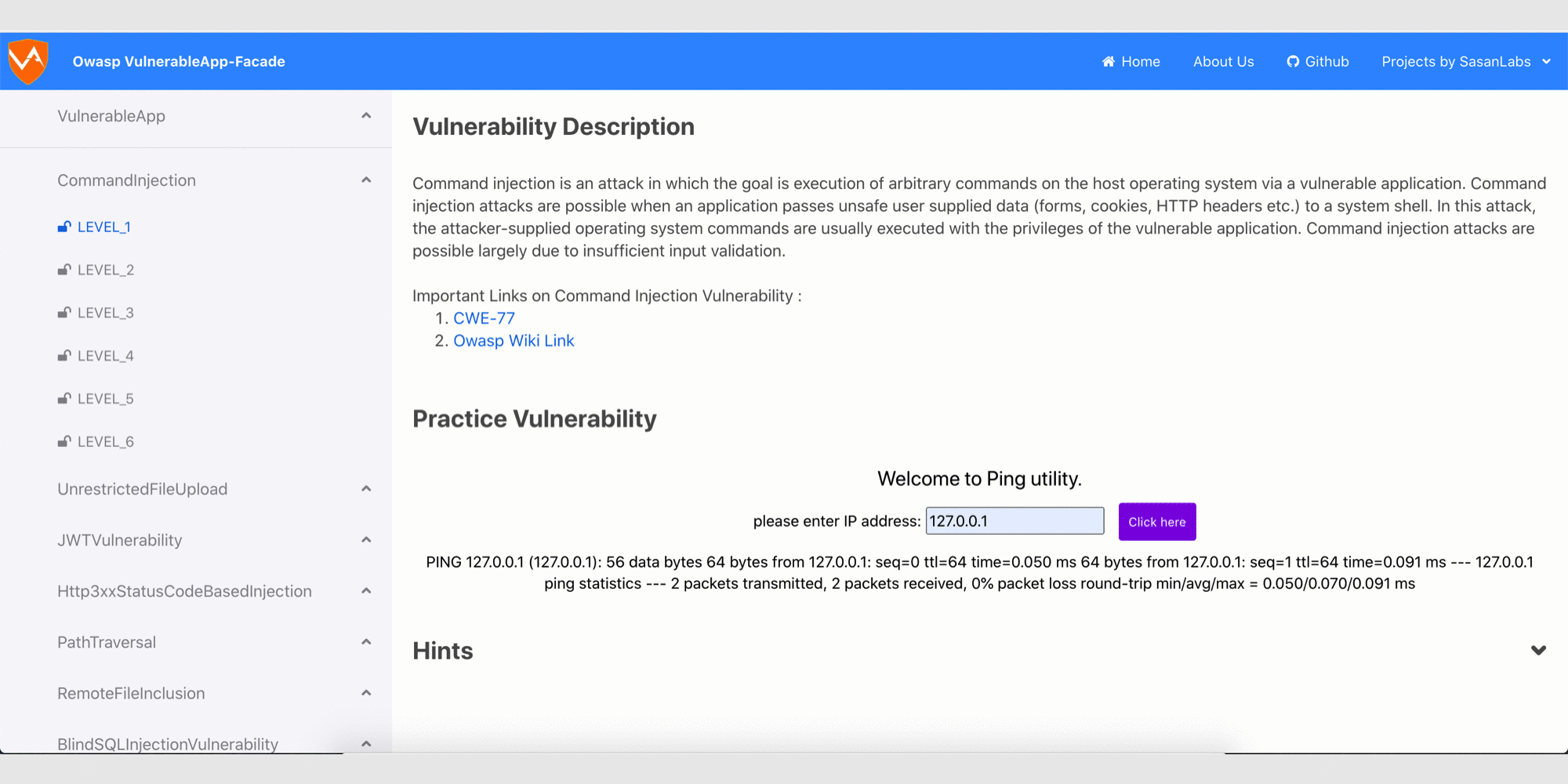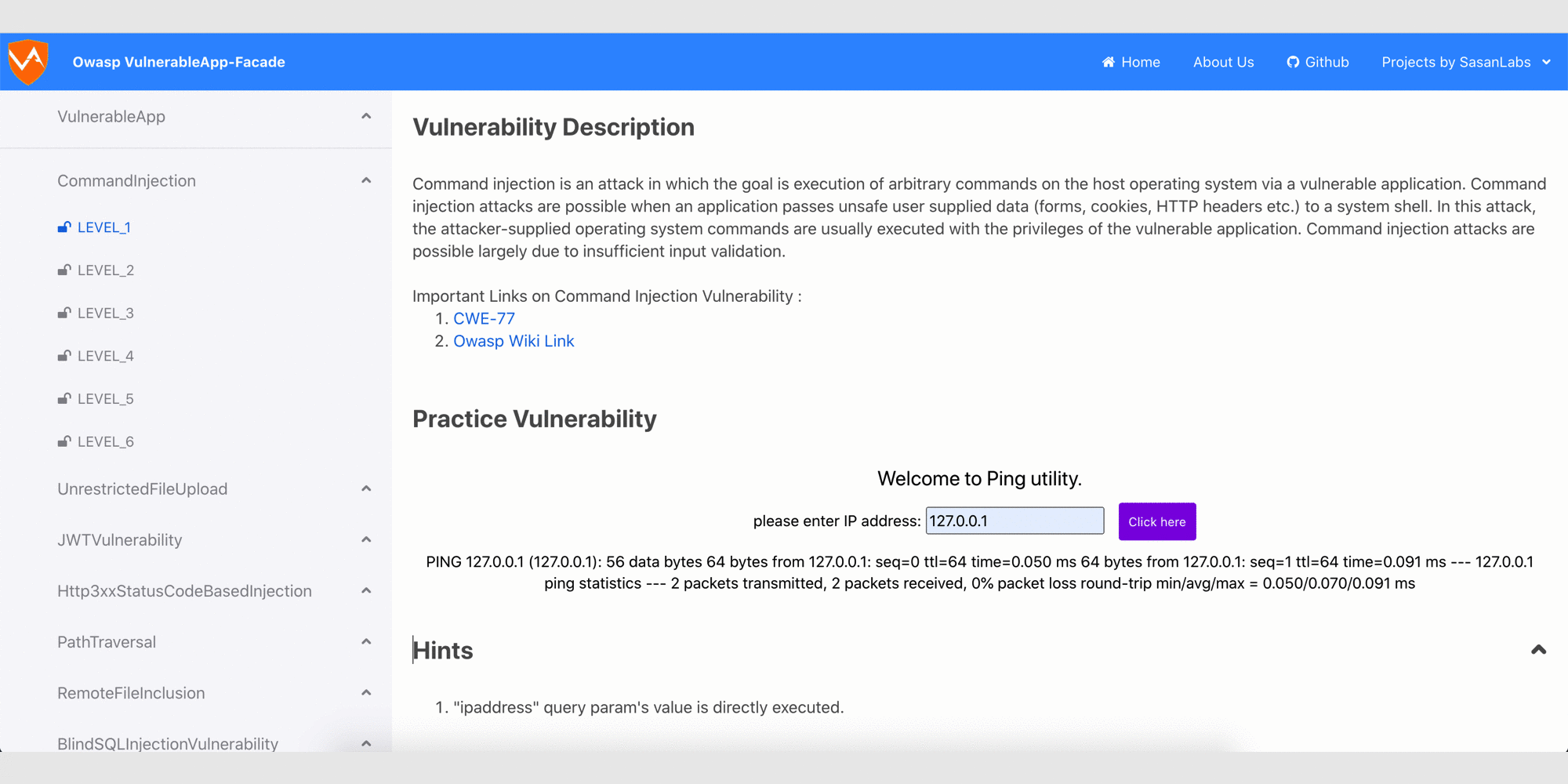
As Web Applications are becoming popular these days, there comes a dire need to secure them. Although there are several Vulnerability Scanning Tools, however while developing these tools, developers need to test them. Moreover, they also need to know how well the Vulnerability Scanning tool is performing. As of now, there are little or no such vulnerable applications existing for testing such tools. There are Deliberately Vulnerable Applications existing in the market but they are not written with such an intent and hence lag extensibility, e.g. adding new vulnerabilities is quite difficult. Hence, developers resort to writing their own vulnerable applications, which usually causes productivity loss and the pain of reworking.
VulnerableApp is built keeping these factors in mind. This project is scalable, extensible, easier to integrate and easier to learn. As solving the above issue requires addition of various vulnerabilities, hence it becomes a very good platform to learn various security vulnerabilities.
User Interface
Technologies used
- Java8
- Spring Boot
- ReactJS
- Javascript/TypeScript
Currently handled Vulnerability types
- JWT Vulnerability
- Command Injection
- File Upload Vulnerability
- Path Traversal Vulnerability
- SQL Injection
- XSS
- XXE
- Open Redirect
- SSRF
Contributing to Project
There are multiple ways in which you can contribute to the project:
- If you are a developer and trying to start on to the project, then the suggestion is to go through the list of issues which contains
good first issuewhich can be a good starter. - If you are a developer or a security professional looking to add new Vulnerability type then you can Generate the Sample Vulnerability by running
./gradlew GenerateSampleVulnerability. It will generate the Sample Vulnerability template which has placeholders and comments. Modified files can be seen in the logs of the command or in the github history. You can navigate to those files, fill in the placeholders and then build the project to see the effect of the changes. - In case you are looking to contribute to the project by publicising it or working on the growth of the project, please feel free to add your thoughts to discussions section or issues and we can discuss over them.
Building the project
There are 2 ways in which this project can be built and used:
- As a Docker application which will help in running the full-fledged VulnerableApplication. For running as Docker application, follow following steps:
- Build the docker image by running
./gradlew jibDockerBuild - Download Docker-Compose and run in the same directory
docker-compose up - Navigate to browser and visit
http://localhostand this will give the User Interface for VulnerableApp.
- Build the docker image by running
- As a SpringBoot application which will run with the Legacy UI or Rest API but gives the benefit of debugging and solving issues. This is the simple way,
- Import the project into your favorite IDE and run it
- Navigate to browser and visit:
http://localhost:9090/VulnerableAppand this will give the Legacy User Interface for VulnerableApp which you can use to debug and test.
Connecting to embedded H2 database
For accessing database from browser, visit: http://localhost:9090/VulnerableApp/h2
Database Connection properties:
JDBC Url: jdbc:h2:mem:testdb
User Name: admin
Password: hacker
Contact
In case you are stuck with any of the steps or understanding anything related to project and its goals, feel free to shoot a mail at [email protected] or raise an issue and we will try our best to help you.
Documentation and References
- Documentation
- Design Documentation
- Owasp VulnerableApp
- Overview video for OWASP Spotlight series
- Overview Video
Blogs
Readme in other languages
Roadmap
Vision for the project:
The overall vision for the project is to implement a Platform capability such that it is easier to write vulnerable code and exposing that through an API and UI.
Usage of the project:
This Project mainly targets 4 type of audience:
- Developers of Vulnerability Scanning tools
- New Vulnerability finders (for faster demonstration of the vulnerability)
- Security enthusiasts, Students who want to learn more about Security
- CTF organizers (A Platform to Host CTF by choosing vulnerabilities present in the project)
Initial high level plan:
Basic idea for this project is to build an extensible framework which is driven by the configuration and developers who want to introduce new vulnerable code into the project need to do minimal boilerplate code and also the learning curve for configurations is minimum.
Looking at it, the first approach which comes into my mind is to give a framework similar to Spring i.e. something like annotation driven framework for including a vulnerability type and also for adding a new vulnerability to existing vulnerability type and also adding User Interface for the same.
- Milestone 1: Alpha release - Building extensible backend Platform
- Milestone 2: Beta release - Building extensible User Interface
- Milestone 3: Gamma release - Addition of 50 vulnerabilities using the above mentioned Platform
- Milestone 4: Release 1
- Milestone 5: Dev lifecycle integration
Current State
For know about the current state please go to Git Repository and also visit issues section for new enhancements,tech-debts and bugs.
Timeframes
This is hard to estimate as this depends on the number of contributers but as of now i had already build some of the pieces of Backend platform and i have started building frontend platform but addition of 50 vulnerabilities can take quite a lot time. So Plan is to release this Project is near July 31 2020.
Technology
Technologies used in this project are:
Majorly:
- Java-8
- SpringBoot
- Vanilla Javascript
- Vanilla CSS
But we are not limited to above technologies and can extend to new Horizons. Incase you have any idea on technology and how it can suit us, please reach out to us on our Slack-Channel.
Challenges
There are many, please visit Issues for more information.



