OWASP Juice Shop

OWASP Juice Shop is probably the most modern and sophisticated insecure web application! It can be used in security trainings, awareness demos, CTFs and as a guinea pig for security tools! Juice Shop encompasses vulnerabilities from the entire OWASP Top Ten along with many other security flaws found in real-world applications!
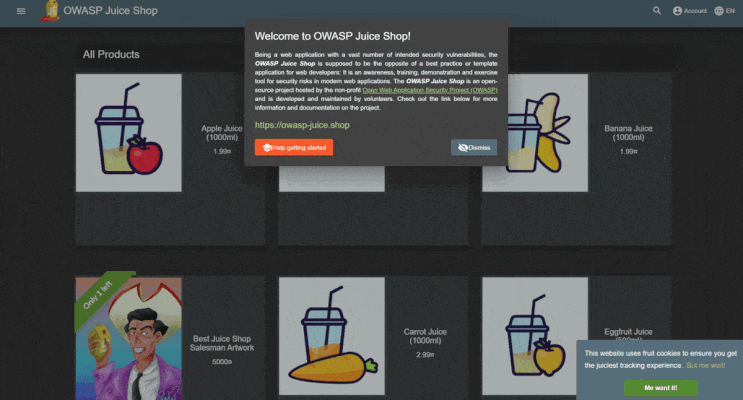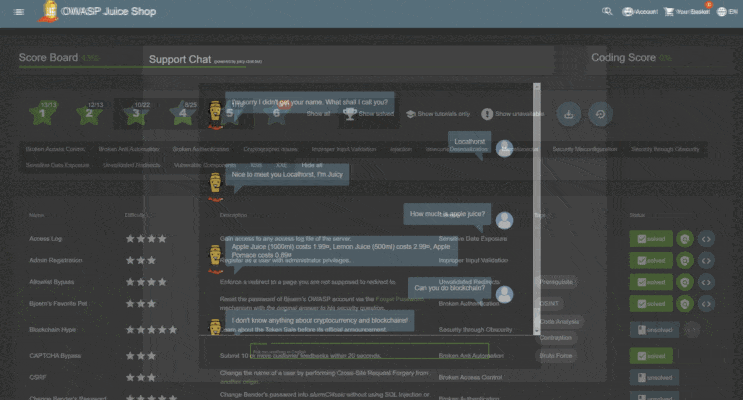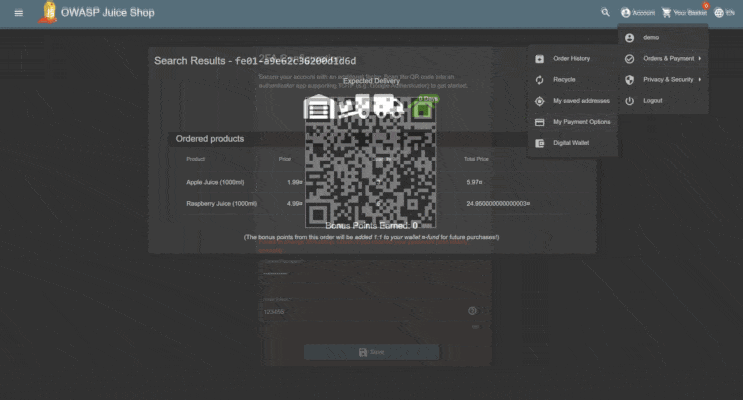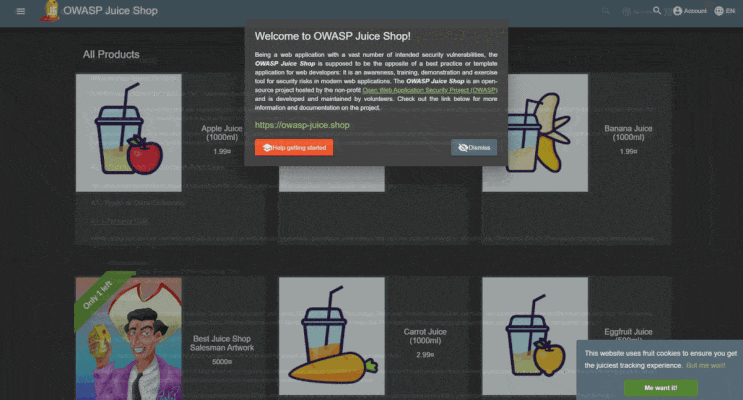
Description
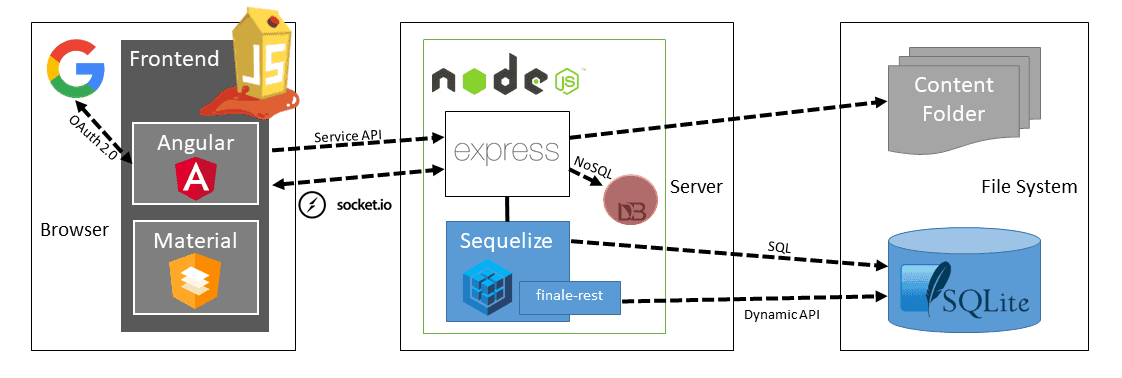
Juice Shop is written in Node.js, Express and Angular. It was the first application written entirely in JavaScript listed in the OWASP VWA Directory.
The application contains a vast number of hacking challenges of varying difficulty where the user is supposed to exploit the underlying vulnerabilities. The hacking progress is tracked on a score board. Finding this score board is actually one of the (easy) challenges!
Apart from the hacker and awareness training use case, pentesting proxies or security scanners can use Juice Shop as a “guinea pig”-application to check how well their tools cope with JavaScript-heavy application frontends and REST APIs.
Translating “dump” or “useless outfit” into German yields “Saftladen” which can be reverse-translated word by word into “juice shop”. Hence the project name. That the initials “JS” match with those of “JavaScript” was purely coincidental!
Testimonials
The most trustworthy online shop out there. ( @dschadow) — The best juice shop on the whole internet! ( @shehackspurple) — Actually the most bug-free vulnerable application in existence! ( @vanderaj) — First you 😂😂then you 😢 ( @kramse) — But this doesn’t have anything to do with juice. ( @coderPatros’ wife)
Contributors
The OWASP Juice Shop has been created by Björn Kimminich and is developed, maintained and translated by a team of volunteers. A live update of the project contributors is found here.
Licensing
This program is free software: You can redistribute it and/or modify it under the terms of the MIT License. OWASP Juice Shop and any contributions are Copyright © by Bjoern Kimminich & the OWASP Juice Shop contributors 2014-2025.
Main Selling Points
- Free and Open source: Licensed under the MIT license with no hidden costs or caveats
- Easy-to-install: Choose between node.js, Docker and Vagrant to run on Windows/Mac/Linux as well as all major cloud providers
- Self-contained: Additional dependencies are pre-packaged or will be resolved and downloaded automatically
- Beginner-friendly: Hacking Instructor scripts with optional tutorial mode guide newcomers through several challenges while explaining the underlying vulnerabilities
- Gamification: The application notifies you on solved challenges and keeps track of successfully exploited vulnerabilities on a Score Board
- Self-healing: Wiped clean and repopulated from scratch on every server startup while automatically persisting progress in your browser or via manual local backup
- Re-branding: Fully customizable in business context and look & feel to your own corporate or customer requirements
- CTF-support: Challenge notifications optionally contain a flag code for your own Capture-The-Flag events
- Coding Challenges: Over 20 hacking challenges come with an additional Coding Challenge where finding and fixing the responsible code flaw can be trained
- Interoperability: Integrate with your own training systems via WebHook, monitor the extensive metrics or consume challenge information directly via API or file import
Screenshots
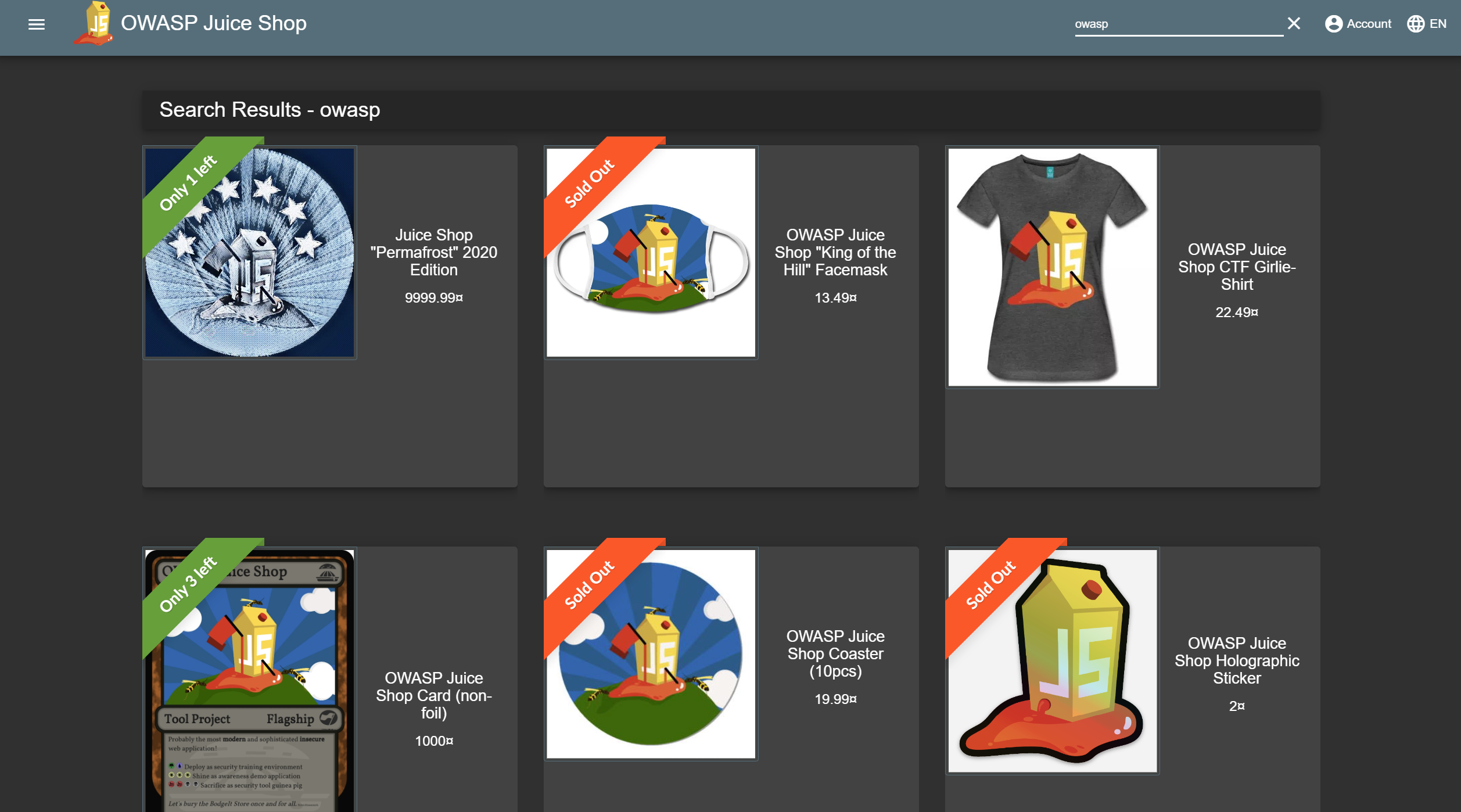
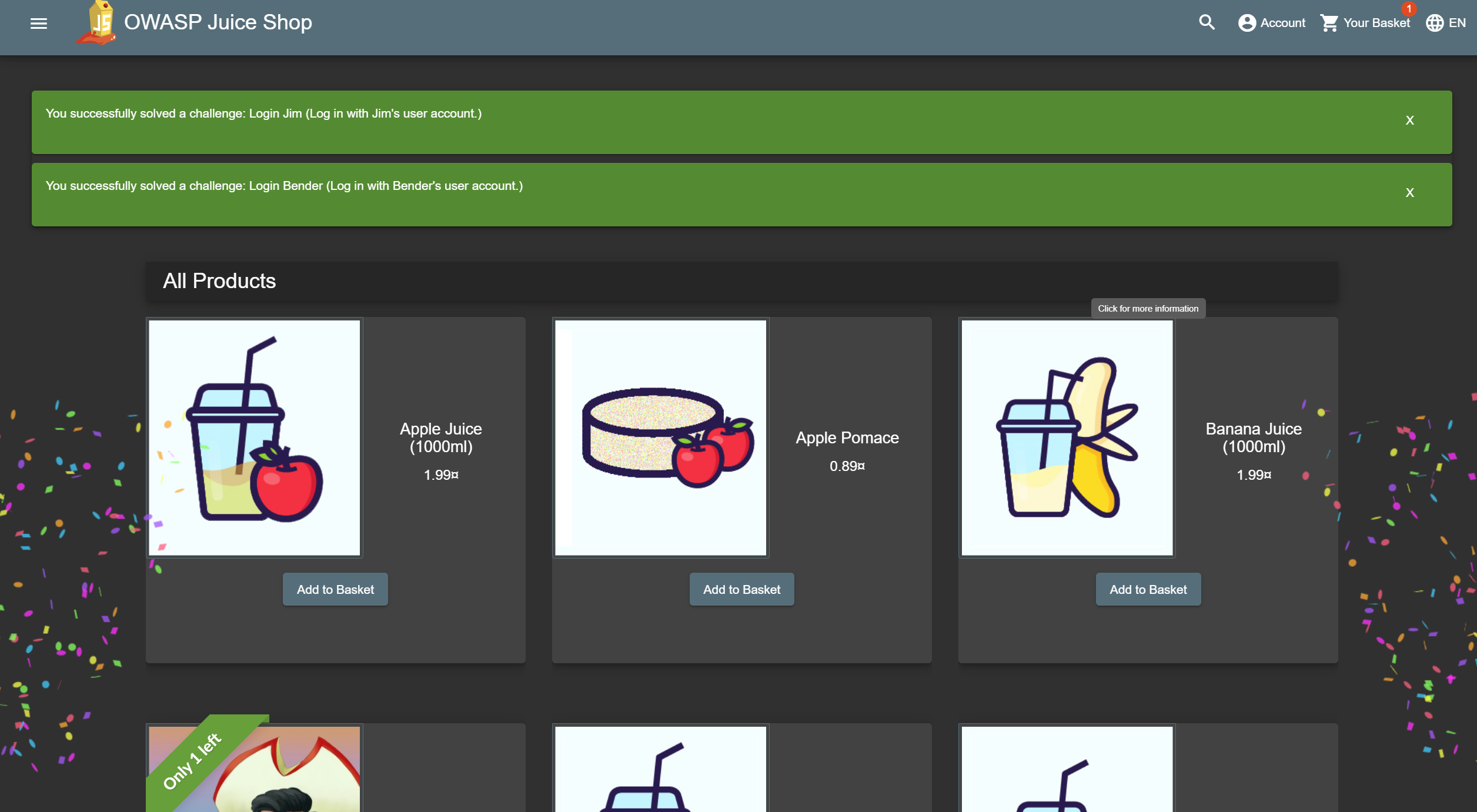
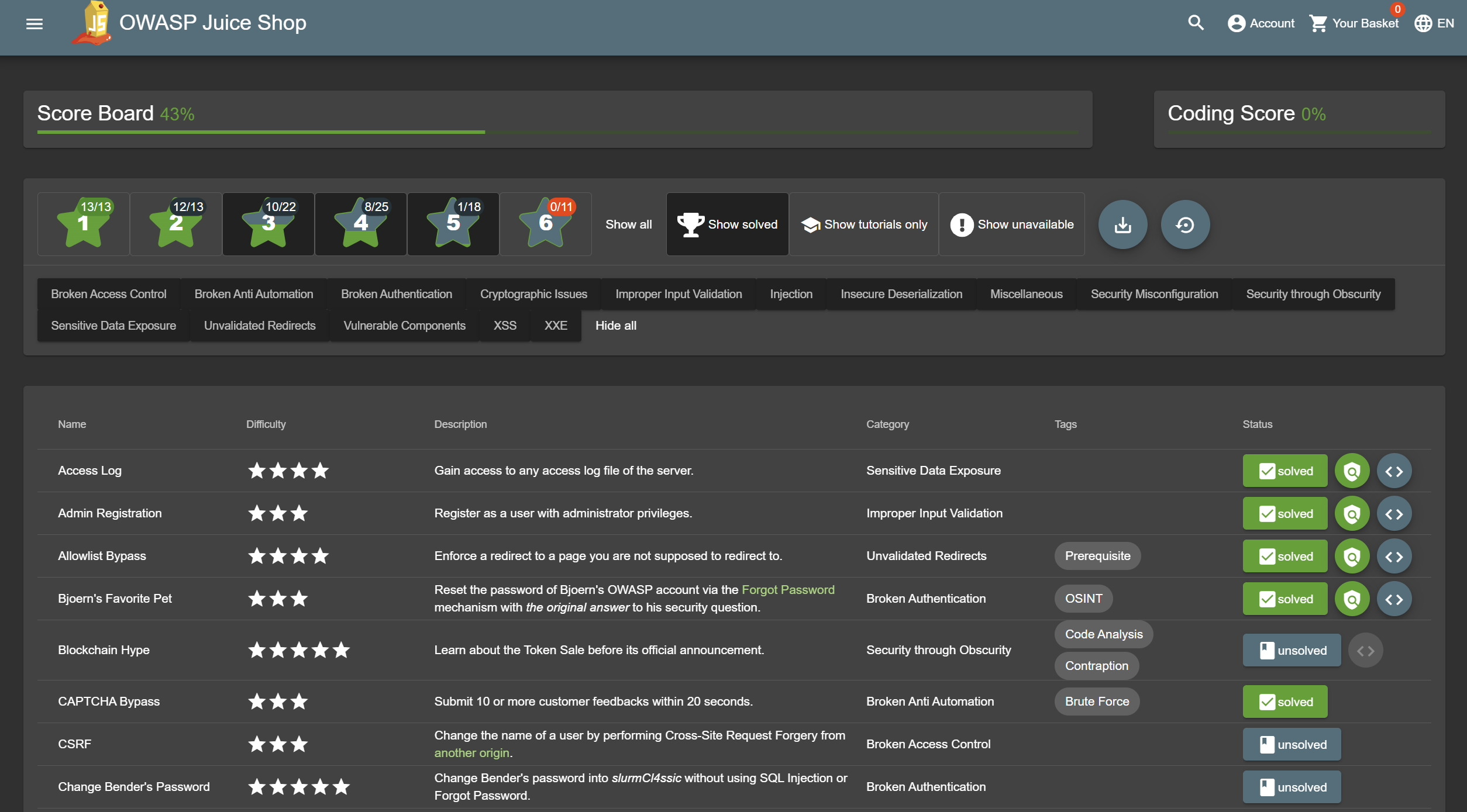
Application Architecture
Latest Releases
- 2025-11-16T14:47:08Z: juice-shop
v19.1.1 - 2025-11-16T13:50:56Z: juice-shop
v19.1.0 - 2025-09-04T05:50:12Z: juice-shop
v19.0.0 - 2025-06-17T05:08:00Z: juice-shop
v18.0.0 - 2025-04-22T22:13:33Z: juice-shop
v17.3.0 - 2025-03-14T21:04:32Z: juice-shop
v17.2.0 - 2024-09-09T16:06:22Z: juice-shop
v17.1.1 - 2024-08-05T15:07:20Z: juice-shop
v17.1.0 - 2024-05-24T21:08:54Z: juice-shop
v17.0.0 - 2024-04-22T13:36:03Z: juice-shop
v16.0.1 - 2023-12-19T15:35:41Z: juice-shop
v16.0.0 - 2023-11-03T20:11:03Z: juice-shop
v15.3.0 - 2023-10-03T21:17:58Z: juice-shop
v15.2.1 - 2023-09-22T16:37:04Z: juice-shop
v15.2.0 - 2023-09-08T13:03:29Z: juice-shop
v15.1.0 - 2023-05-19T23:00:51Z: juice-shop
v15.0.0
CTF Extension
- 2025-09-04T06:11:47Z: juice-shop-ctf
v12.0.0 - 2025-02-18T11:19:13Z: juice-shop-ctf
v11.1.0 - 2024-10-25T14:30:28Z: juice-shop-ctf
v11.0.0 - 2023-10-11T22:23:15Z: juice-shop-ctf
v10.0.1 - 2023-09-01T10:31:42Z: juice-shop-ctf
v10.0.0 - 2022-08-23T16:13:55Z: juice-shop-ctf
v9.1.2 - 2022-08-03T04:31:18Z: juice-shop-ctf
v9.1.1
MultiJuicer
- 2026-02-12T19:50:54Z: multi-juicer
v9.2.0 - 2026-01-25T21:15:53Z: multi-juicer
v9.1.0 - 2025-11-22T17:39:28Z: multi-juicer
v9.0.0 - 2025-06-17T07:57:20Z: multi-juicer
v8.3.0 - 2025-04-30T09:15:52Z: multi-juicer
v8.2.0 - 2025-03-15T18:57:18Z: multi-juicer
v8.1.0 - 2025-03-05T18:29:42Z: multi-juicer
v8.0.5 - 2025-02-27T13:10:39Z: multi-juicer
v8.0.4 - 2025-02-25T19:43:35Z: multi-juicer
v8.0.3 - 2025-02-07T14:54:23Z: multi-juicer
v8.0.2 - 2025-01-07T18:42:57Z: multi-juicer
v8.0.1 - 2024-12-28T13:51:39Z: multi-juicer
v8.0.0 - 2024-10-06T00:25:23Z: multi-juicer
v7.3.2 - 2024-09-19T13:26:34Z: multi-juicer
v7.3.1 - 2024-09-10T09:40:37Z: multi-juicer
v7.3.0
Roadmap

-
Enhance UX of Score Board regarding coding challenges and embedded payloads (#2875, #2876)
-
Modernize the frontend for better maintainability, performance, and accessibility (#2868)
-
Investigate possibility to include AI/LLM challenges without bloating the application
-
Gradually enhance the codebase and pay back accumulated technical debt
-
Eventually bring overall test coverage back over 90%
Challenge Categories
The vulnerabilities found in the OWASP Juice Shop are categorized into several different classes. Most of them cover different risk or vulnerability types from well-known lists or documents, such as OWASP Top 10, OWASP ASVS, OWASP Automated Threat Handbook and OWASP API Security Top 10 or MITRE’s Common Weakness Enumeration.
| Category | # | Challenges |
|---|---|---|
| Broken Access Control | 11 | Admin Section, CSRF, Easter Egg, Five-Star Feedback, Forged Feedback, Forged Review, Manipulate Basket, Product Tampering, SSRF, View Basket, Web3 Sandbox |
| Broken Anti Automation | 4 | CAPTCHA Bypass, Extra Language, Multiple Likes, Reset Morty's Password |
| Broken Authentication | 9 | Bjoern's Favorite Pet, Change Bender's Password, GDPR Data Erasure, Login Bjoern, Password Strength, Reset Bender's Password, Reset Bjoern's Password, Reset Jim's Password, Two Factor Authentication |
| Cryptographic Issues | 5 | Forged Coupon, Imaginary Challenge, Nested Easter Egg, Premium Paywall, Weird Crypto |
| Improper Input Validation | 12 | Admin Registration, Deluxe Fraud, Empty User Registration, Expired Coupon, Mint the Honey Pot, Missing Encoding, Payback Time, Poison Null Byte, Repetitive Registration, Upload Size, Upload Type, Zero Stars |
| Injection | 11 | Christmas Special, Database Schema, Ephemeral Accountant, Login Admin, Login Bender, Login Jim, NoSQL DoS, NoSQL Exfiltration, NoSQL Manipulation, SSTi, User Credentials |
| Insecure Deserialization | 3 | Blocked RCE DoS, Memory Bomb, Successful RCE DoS |
| Miscellaneous | 7 | Bully Chatbot, Mass Dispel, Privacy Policy, Score Board, Security Advisory, Security Policy, Wallet Depletion |
| Observability Failures | 4 | Access Log, Exposed Metrics, Leaked Access Logs, Misplaced Signature File |
| Security Misconfiguration | 4 | Cross-Site Imaging, Deprecated Interface, Error Handling, Login Support Team |
| Security through Obscurity | 3 | Blockchain Hype, Privacy Policy Inspection, Steganography |
| Sensitive Data Exposure | 15 | Confidential Document, Email Leak, Exposed credentials, Forgotten Developer Backup, Forgotten Sales Backup, GDPR Data Theft, Leaked API Key, Leaked Unsafe Product, Login Amy, Login MC SafeSearch, Meta Geo Stalking, NFT Takeover, Reset Uvogin's Password, Retrieve Blueprint, Visual Geo Stalking |
| Unvalidated Redirects | 2 | Allowlist Bypass, Outdated Allowlist |
| Vulnerable Components | 9 | Arbitrary File Write, Forged Signed JWT, Frontend Typosquatting, Kill Chatbot, Legacy Typosquatting, Local File Read, Supply Chain Attack, Unsigned JWT, Vulnerable Library |
| XSS | 9 | API-only XSS, Bonus Payload, CSP Bypass, Client-side XSS Protection, DOM XSS, HTTP-Header XSS, Reflected XSS, Server-side XSS Protection, Video XSS |
| XXE | 2 | XXE Data Access, XXE DoS |
| Total Σ | 110 | |
Challenge Tags
Tags do not represent vulnerability categories but serve as additional meta information for challenges. They mark certain commonalities or special types of challenges - like those lacking seriousness or ones that probably need some scripting/automation etc.
| Tag | # | Challenges |
|---|---|---|
| Brute Force | 6 | Bully Chatbot, CAPTCHA Bypass, Extra Language, Login Support Team, Password Strength, Reset Morty's Password |
| Code Analysis | 10 | Blockchain Hype, Forged Coupon, Imaginary Challenge, Kill Chatbot, Login Bjoern, Login Support Team, Outdated Allowlist, SSRF, SSTi, Score Board |
| Contraption | 9 | Blockchain Hype, Cross-Site Imaging, Deprecated Interface, Easter Egg, Forgotten Developer Backup, Forgotten Sales Backup, Misplaced Signature File, NFT Takeover, SSTi |
| Danger Zone | 17 | API-only XSS, Arbitrary File Write, Blocked RCE DoS, CSP Bypass, Client-side XSS Protection, HTTP-Header XSS, Local File Read, Memory Bomb, NoSQL DoS, NoSQL Exfiltration, Reflected XSS, SSTi, Server-side XSS Protection, Successful RCE DoS, Video XSS, XXE Data Access, XXE DoS |
| Good Practice | 4 | Exposed Metrics, Misplaced Signature File, Privacy Policy, Security Policy |
| Good for Demos | 13 | Admin Section, Confidential Document, DOM XSS, Easter Egg, Forged Coupon, Forgotten Developer Backup, Login Admin, NFT Takeover, Nested Easter Egg, Privacy Policy, Privacy Policy Inspection, Reflected XSS, View Basket |
| Internet Traffic | 2 | Mint the Honey Pot, Wallet Depletion |
| OSINT | 15 | Bjoern's Favorite Pet, Leaked Access Logs, Leaked Unsafe Product, Local File Read, Login Amy, Login MC SafeSearch, Meta Geo Stalking, Reset Bender's Password, Reset Bjoern's Password, Reset Jim's Password, Reset Morty's Password, Reset Uvogin's Password, Supply Chain Attack, Visual Geo Stalking, Vulnerable Library |
| Prerequisite | 6 | Allowlist Bypass, Arbitrary File Write, Deprecated Interface, Error Handling, Forgotten Developer Backup, Poison Null Byte |
| Shenanigans | 11 | Bonus Payload, Bully Chatbot, Easter Egg, Imaginary Challenge, Leaked Unsafe Product, Login MC SafeSearch, Missing Encoding, Nested Easter Egg, Premium Paywall, Privacy Policy Inspection, Steganography |
| Tutorial | 11 | Bonus Payload, DOM XSS, Forged Feedback, Login Admin, Login Bender, Login Jim, Password Strength, Privacy Policy, Reflected XSS, Score Board, View Basket |
| Web3 | 5 | Blockchain Hype, Mint the Honey Pot, NFT Takeover, Wallet Depletion, Web3 Sandbox |
Hacking Instructor Tutorials

Click on a link in the table below to launch a step-by-step tutorial for that particular challenge on our public https://demo.owasp-juice.shop instance. If you are entirely new to the Juice Shop, we recommend doing them in the listed order. With the (optional) Tutorial Mode you can even enforce that the 13 tutorial challenges have to be performed gradually in order to unlock the other 97 challenges.
| Challenge | Category | Difficulty |
|---|---|---|
| Score Board | Miscellaneous | ⭐ |
| DOM XSS | XSS | ⭐ |
| Bonus Payload | XSS | ⭐ |
| Privacy Policy | Miscellaneous | ⭐ |
| Reflected XSS | XSS | ⭐⭐ |
| Exposed credentials | Sensitive Data Exposure | ⭐⭐ |
| Login Admin | Injection | ⭐⭐ |
| Admin Section | Broken Access Control | ⭐⭐ |
| Password Strength | Broken Authentication | ⭐⭐ |
| View Basket | Broken Access Control | ⭐⭐ |
| Forged Feedback | Broken Access Control | ⭐⭐⭐ |
| Login Jim | Injection | ⭐⭐⭐ |
| Login Bender | Injection | ⭐⭐⭐ |
| Coding Challenges | n/a | n/a |
Coding Challenges
For 31 challenges an additional coding challenge is available. In their “Find It” phase they teach
spotting vulnerabilities in the actual codebase of the Juice Shop. In the “Fix It” phase the user then chooses the most appropriate
fix from a list. Solve any of the hacking challenges below to enable a button on the Score Board that launches the corresponding
coding challenge:
| Category | # | Challenges |
|---|---|---|
| Broken Access Control | 4 | Admin Section, Forged Review, Product Tampering, Web3 Sandbox |
| Broken Anti Automation | 1 | Reset Morty's Password |
| Broken Authentication | 5 | Bjoern's Favorite Pet, Password Strength, Reset Bender's Password, Reset Bjoern's Password, Reset Jim's Password |
| Improper Input Validation | 2 | Admin Registration, Mint the Honey Pot |
| Injection | 6 | Database Schema, Login Admin, Login Bender, Login Jim, NoSQL Manipulation, User Credentials |
| Miscellaneous | 2 | Score Board, Wallet Depletion |
| Observability Failures | 2 | Access Log, Exposed Metrics |
| Security through Obscurity | 1 | Blockchain Hype |
| Sensitive Data Exposure | 3 | Confidential Document, NFT Takeover, Reset Uvogin's Password |
| Unvalidated Redirects | 2 | Allowlist Bypass, Outdated Allowlist |
| XSS | 3 | API-only XSS, Bonus Payload, DOM XSS |
| Total Σ | 31 | |
Mitigation Links
For many solved challenges links to mitigation techniques are presented on the Score Board by offering a link to a corresponding OWASP Cheat Sheet explaining how to avoid that kind of vulnerability in the first place. The following cheat sheets are referred to by OWASP Juice Shop as mitigation links:
- Authentication Cheat Sheet
- Authorization Cheat Sheet
- Choosing and Using Security Questions Cheat Sheet
- Credential Stuffing Prevention Cheat Sheet
- Cross-Site Request Forgery Prevention Cheat Sheet
- Cross Site Scripting Prevention Cheat Sheet
- Cryptographic Storage Cheat Sheet
- DOM based XSS Prevention Cheat Sheet
- Denial of Service Cheat Sheet
- Error Handling Cheat Sheet
- File Upload Cheat Sheet
- Forgot Password Cheat Sheet
- Injection Prevention Cheat Sheet
- Input Validation Cheat Sheet
- JSON Web Token for Java Cheat Sheet
- Key Management Cheat Sheet
- Logging Cheat Sheet
- Mass Assignment Cheat Sheet
- Multifactor Authentication Cheat Sheet
- REST Security Cheat Sheet
- SQL Injection Prevention Cheat Sheet
- Secrets Management Cheat Sheet
- Server Side Request Forgery Prevention Cheat Sheet
- Unvalidated Redirects and Forwards Cheat Sheet
- User Privacy Protection Cheat Sheet
- Vulnerability Disclosure Cheat Sheet
- Vulnerable Dependency Management Cheat Sheet
- Web Service Security Cheat Sheet
- XML External Entity Prevention Cheat Sheet
- XS Leaks Cheat Sheet
CTF Extension

The Node package
juice-shop-ctf-cli
helps you to prepare
Capture the Flag
events with the OWASP Juice Shop challenges for different popular CTF
frameworks. This interactive utility allows you to populate a CTF game
server in a matter of minutes.
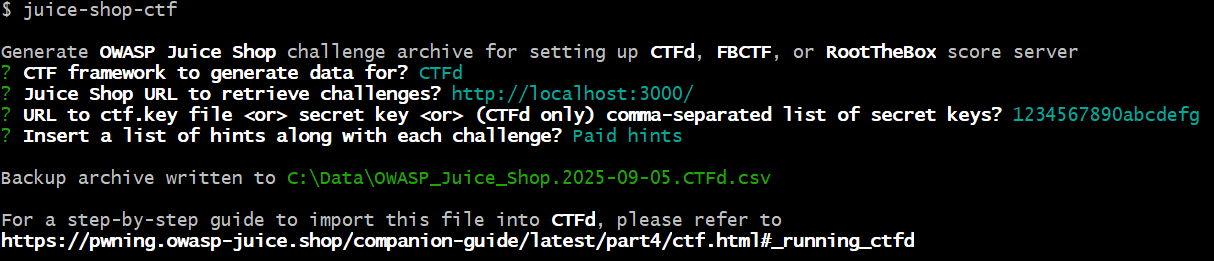
Supported CTF Frameworks
The following open source CTF frameworks are supported by
juice-shop-ctf-cli:
Official Companion Guide
Pwning OWASP Juice Shop is the official companion guide for this project. It will give you a complete overview of the vulnerabilities found in the application including hints how to spot and exploit them. In the appendix you will even find complete step-by-step solutions to every challenge.
The ebook is published under CC BY-NC-ND 4.0 and is online-readable for free at https://pwning.owasp-juice.shop. The latest officially released edition is also available for free at https://leanpub.com/juice-shop in PDF, Kindle and ePub format.
Official Multi User Platform
Multi User Juice Shop Platform to run separate Juice Shop instances for training or CTF participants on a central Kubernetes cluster. MultiJuicer comes with a built-in leader board and its own dedicated Juice Balancer for instance isolation.
Official Jingle
Official OWASP Juice Shop Jingle written and performed by Brian Johnson
Endorsed Open Source Projects
| Project | Description |
|---|---|
| https://github.com/wurstbrot/shake-logger | Demo to show the dangers of XSS holes combined with bad Content Security Policy using Harlem Shake and a Keylogger against the Juice Shop (📺YouTube) |
The tools listed above are provided by third parties outside the OWASP Juice Shop project scope. For support or feature requests please use the support channels or issue trackers mentioned by these projects.
Project Supporters
You can attribute your donation to the OWASP Juice Shop project by using this link or the green “Donate”-button while on any tab of the Juice Shop project page!
Top Supporters
In order to be recognized as a “Top Supporter” a company must have donated $1000 or more a) to OWASP while attributing it to Juice Shop or b) as a restricted gift to OWASP Juice Shop in the last 12 months.
All Corporate Supporters
- secuvera(2018/2019/2023)
- mindsetters OG(2023)
- Heyhack(2022)
- Schutzwerk(2022)
- New Work SE(2019/2021)
- RandoriSec(2021)
- Wild West Hackin’ Fest(2020)
- Denim Group(2018-2019)
- PlexTrac(2019)
- Silpion(2019)
- iteratec(2017)
- eSailors(2016)
- XING(2016)
All Individual Supporters
-
Björn Kimminich
-
Jeroen Willemsen
-
Soron Foster
-
Bendik Mjaaland
-
Timo Pagel
-
Benjamin Pfänder
-
Kevin Chung
-
Brian Johnson
-
Omar Santos
-
Merlyn Albery
-
Alper Basaran
-
Jediah Logiodice
-
Kenyo Kaneda
-
Ian Sexton
-
David @ HailBytes
-
You want to appear on this list? Donate to OWASP here! 🤲
All Corporate-sponsored Code Contributions
- #1221, #1356: Panasonic Information Systems Company Europe(2019-2020)
In order to be recognized as a “Corporate-sponsored Code Contribution” an official written confirmation of waiving all IP to the contributed code must be formally submitted to the OWASP Foundation.
LeanPub Royalties
$1,251.68 of royalties from Björn Kimminich’s eBook have been donated to the project between 09/2017 and 07/2019.
MultiJuicer Maintenance
MultiJuicer was originally developed (and is still maintained primarily) by iteratec. It became an official part of the OWASP Juice Shop project 05/2023.

The OWASP Foundation is very grateful for the support by the individuals and organizations listed. However, please note, the OWASP Foundation is strictly vendor neutral and does not endorse any of its supporters.























