WSTG - Latest
Testing WebSockets
| ID |
|---|
| WSTG-CLNT-10 |
Summary
Traditionally, the HTTP protocol only allows one request/response per TCP connection. Asynchronous JavaScript and XML (AJAX) allows clients to send and receive data asynchronously (in the background without a page refresh) to the server, however, AJAX requires the client to initiate the requests and wait for the server responses (half-duplex).
WebSockets allow the client or server to create a ‘full-duplex’ (two-way) communication channel, allowing the client and server to truly communicate asynchronously. WebSockets conduct their initial upgrade handshake over HTTP and from then on all communication is carried out over TCP channels by use of frames. For more, see the WebSocket Protocol.
Origin
It is the server’s responsibility to verify the Origin header in the initial HTTP WebSocket handshake. If the server does not validate the origin header in the initial WebSocket handshake, the WebSocket server may accept connections from any origin. This could allow attackers to communicate with the WebSocket server cross-domain allowing for CSRF-like issues. See also Top 10-2017 A5-Broken Access Control. The exploit for this weakness is called Cross-Site Websocket Hijacking (CSWH or CSWSH).
Confidentiality and Integrity
WebSockets can be used over unencrypted TCP or over encrypted TLS. To use unencrypted WebSockets the ws:// URI scheme is used (default port 80), to use encrypted (TLS) WebSockets the wss:// URI scheme is used (default port 443). See also Top 10-2017 A3-Sensitive Data Exposure.
Input Sanitization
As with any data originating from untrusted sources, the data should be properly sanitized and encoded. See also Top 10-2017 A1-Injection and Top 10-2017 A7-Cross-Site Scripting (XSS).
Test Objectives
- Identify the usage of WebSockets.
- Assess its implementation by using the same tests on normal HTTP channels.
How to Test
Black-Box Testing
- Identify that the application is using WebSockets.
- Inspect the client-side source code for the
ws://orwss://URI scheme. - Use Google Chrome’s Developer Tools to view the Network WebSocket communication.
- Use ZAP’s WebSocket tab.
- Inspect the client-side source code for the
- Origin.
- Using a WebSocket client (one can be found in the Tools section below) attempt to connect to the remote WebSocket server. If a connection is established the server may not be checking the origin header of the WebSocket handshake.
- Confidentiality and Integrity.
- Check that the WebSocket connection is using TLS to transport sensitive information
wss://. - Check the HTTPS Implementation for security issues (Valid Certificate, BEAST, CRIME, RC4, etc). Refer to the Testing for Weak Transport Layer Security section of this guide.
- Check that the WebSocket connection is using TLS to transport sensitive information
- Authentication.
- WebSockets do not handle authentication, normal black-box authentication tests should be carried out. Refer to the Authentication Testing sections of this guide.
- Authorization.
- WebSockets do not handle authorization, normal black-box authorization tests should be carried out. Refer to the Authorization Testing sections of this guide.
- Input Sanitization.
- Use ZAP’s WebSocket tab to replay and fuzz WebSocket request and responses. Refer to the Testing for Data Validation sections of this guide.
Example 1
Once we have identified that the application is using WebSockets (as described above) we can use the Zed Attack Proxy (ZAP) to intercept the WebSocket request and responses. ZAP can then be used to replay and fuzz the WebSocket request/responses.
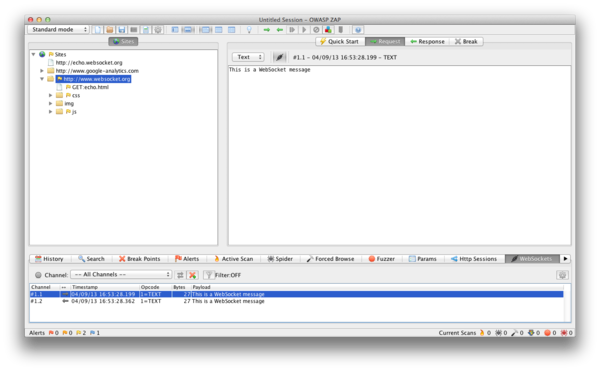
Figure 4.11.10-1: ZAP WebSockets
Example 2
Using a WebSocket client (one can be found in the Tools section below) attempt to connect to the remote WebSocket server. If the connection is allowed the WebSocket server may not be checking the WebSocket handshake’s origin header. Attempt to replay requests previously intercepted to verify that cross-domain WebSocket communication is possible.
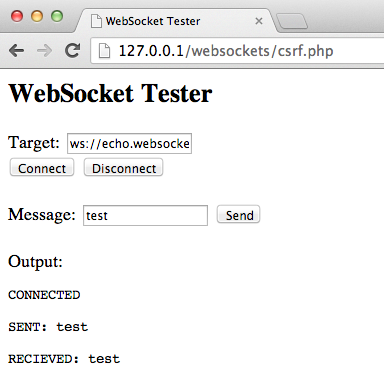
Figure 4.11.10-2: WebSocket Client
Gray-Box Testing
Gray-box testing is similar to black-box testing. In gray-box testing, the pen-tester has partial knowledge of the application. The only difference here is that you may have API documentation for the application being tested which includes the expected WebSocket request and responses.
Tools
References
- HTML5 Rocks - Introducing WebSockets: Bringing Sockets to the Web
- W3C - The WebSocket API
- IETF - The WebSocket Protocol
- CWE-1385: Missing Origin Validation in WebSockets
- Christian Schneider - Cross-Site WebSocket Hijacking (CSWSH)
- Robert Koch- On WebSockets in Penetration Testing
- DigiNinja - ZAP and Web Sockets